
Millennials Pose a Greater Security Risk
 Millennials Pose a Greater Security Risk
Millennials Pose a Greater Security Risk
By Karen A. Frenkel
 Who’s Responsible for Security?
Who’s Responsible for Security?
50% of respondents said security is not their responsibility and 30% said there should be no penalty for losing company data. 78% think their company clearly communicates to them about security best practices.
 Boomers vs. Millennials
Boomers vs. Millennials
5% of Baby Boomers believe they compromise IT security, whereas 25% Millennials think so.
 Work Devices for Personal Use
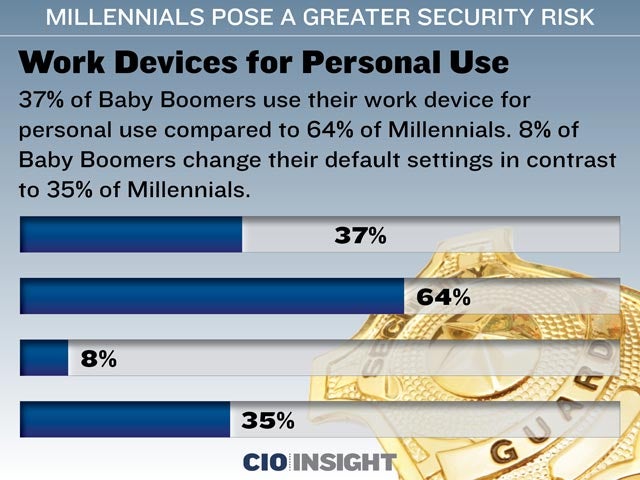
Work Devices for Personal Use
37% of Baby Boomers use their work device for personal use compared to 64% of Millennials. 8% of Baby Boomers change their default settings in contrast to 35% of Millennials.
 Device Use
Device Use
Respondents use a plethora of devices, according to this breakout: 1 device: 46%, 2 devices: 37%, 3 devices: 12%, 4 devices: 4%
 Security Risk by Position Level
Security Risk by Position Level
Senior, mid-level and junior level employees have very different perceptions of their device’s security risks. 33% of senior-level professionals think their device is not safe for work, compared to 19% and 9% of mid-level and junior personnel, respectively.
 Personal Use of Company Devices
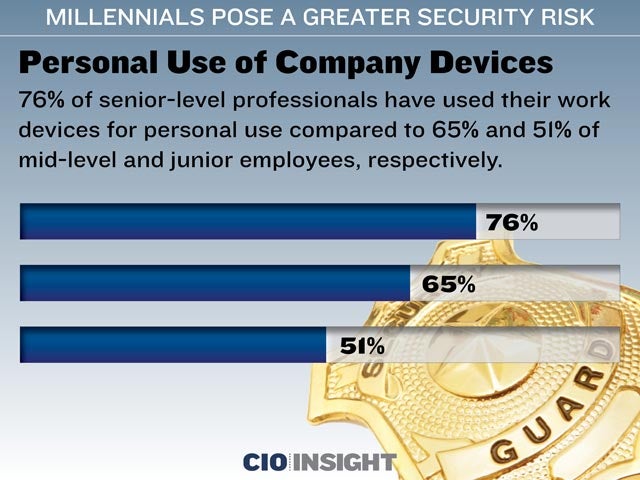
Personal Use of Company Devices
76% of senior-level professionals have used their work devices for personal use compared to 65% and 51% of mid-level and junior employees, respectively.
 Loss of Device
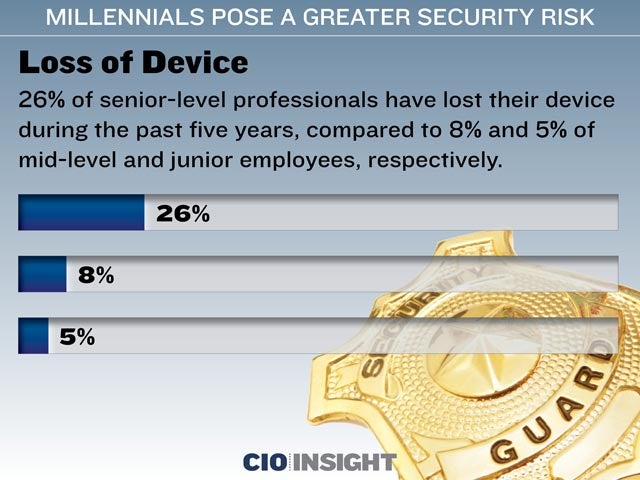
Loss of Device
26% of senior-level professionals have lost their device during the past five years, compared to 8% and 5% of mid-level and junior employees, respectively.
 Perceived Value of Data
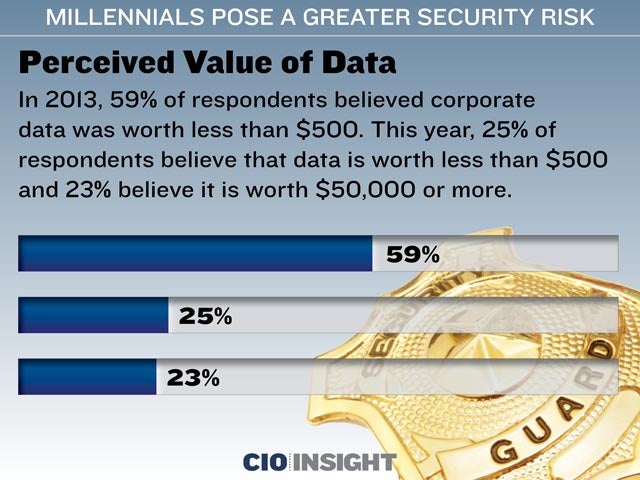
Perceived Value of Data
In 2013, 59% of respondents believed corporate data was worth less than $500. This year, 25% of respondents believe that data is worth less than $500 and 23% believe it is worth $50,000 or more.
 Benefits of Mobility
Benefits of Mobility
Asked what they consider the greatest benefit of mobile, respondents said: Ability to respond to requests from any location: 39%, Work while travel: 38%, Able to bring device to meetings at work: 31%, More flexible during working hours: 29%, Can access corporate data remotely: 28%
 Mitigating Security Risks Through Education
Mitigating Security Risks Through Education
The report recommends: Training employees on best practices, Maintaining updated IT security policy, Building policies to address employee behaviors that may put sensitive data at risk
 Ways IT Can Mitigate Security
Ways IT Can Mitigate Security
For the IT Department, the report recommends implementing security that gives IT visibility over all devices on or off the network and applying a layered approach to data security including encryption, remote endpoint security capabilities and anti-malware.