
Confusion over Security Responsibility in Cloud
 Confusion over Security Responsibility in Cloud
Confusion over Security Responsibility in Cloud
IT professionals are migrating to the cloud, yet they are unclear about public cloud shared responsibility for security.
 IT Professionals Ignorant of Shared Responsibility in the Cloud
IT Professionals Ignorant of Shared Responsibility in the Cloud
40 percent of respondents believe that their cloud service provider protects their applications and data. 34 percent believe security is their own company’s responsibility.
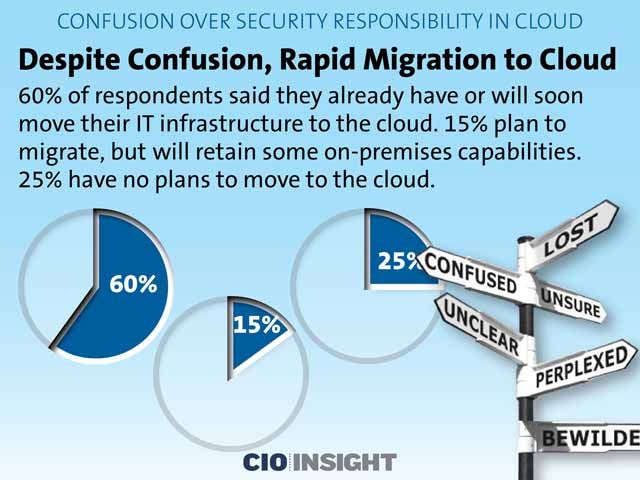 Despite Confusion, Rapid Migration to Cloud
Despite Confusion, Rapid Migration to Cloud
60 percent of respondents said they already have or will soon move their IT infrastructure to the cloud. 15 percent plan to migrate, but will retain some on-premises capabilities. 25 percent have no plans to move to the cloud.
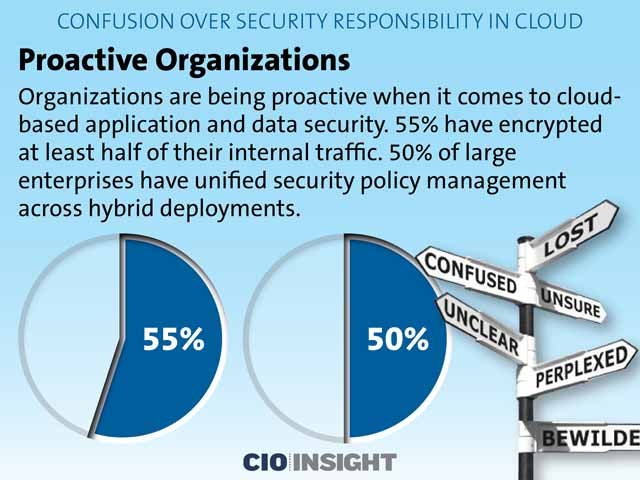 Proactive Organizations
Proactive Organizations
Organizations are being proactive when it comes to cloud-based application and data security. 55 percent have encrypted at least half of their internal traffic. 50 percent of large enterprises have unified security policy management across hybrid deployments.
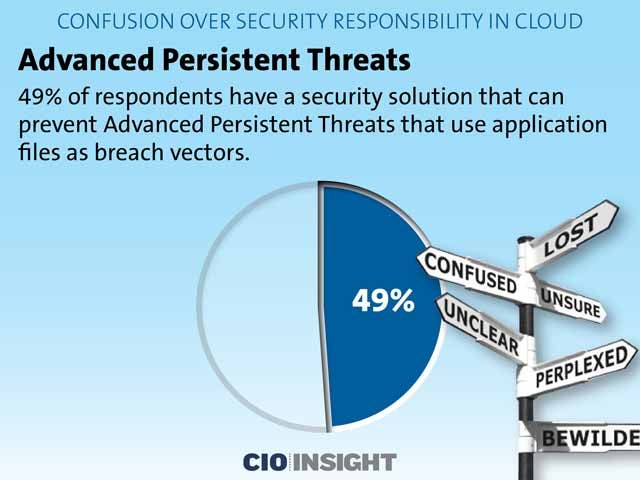 Advanced Persistent Threats
Advanced Persistent Threats
49 percent of respondents have a security solution that can prevent Advanced Persistent Threats that use application files as breach vectors.
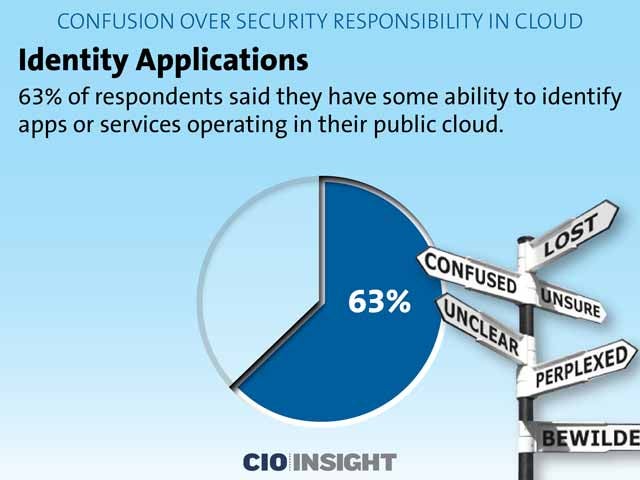 Identity Applications
Identity Applications
63 percent of respondents said they have some ability to identify apps or services operating in their public cloud.
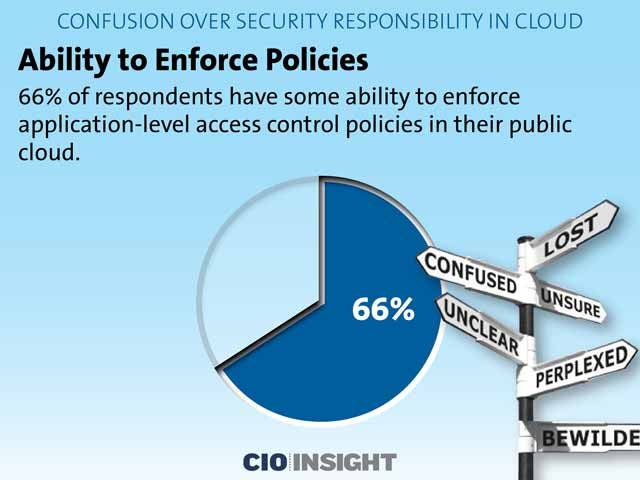 Ability to Enforce Policies
Ability to Enforce Policies
66 percent of respondents have some ability to enforce application-level access control policies in their public cloud.
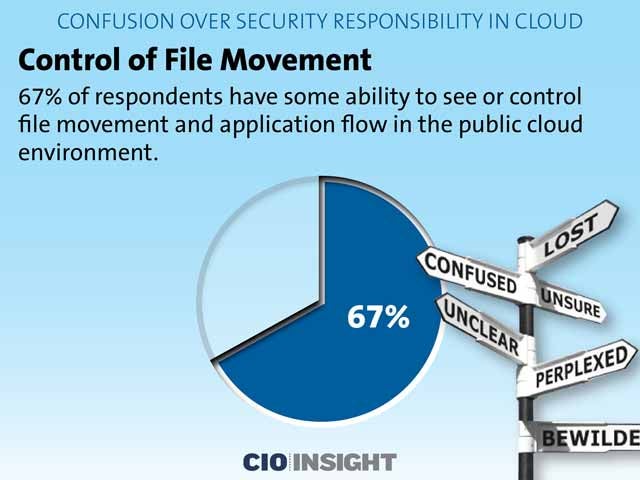 Control of File Movement
Control of File Movement
67 percent of respondents have some ability to see or control file movement and application flow in the public cloud environment.
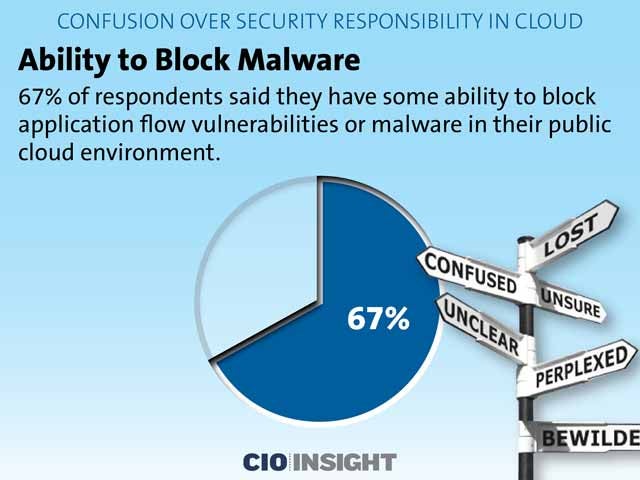 Ability to Block Malware
Ability to Block Malware
67 percent of respondents said they have some ability to block application flow vulnerabilities or malware in their public cloud environment.
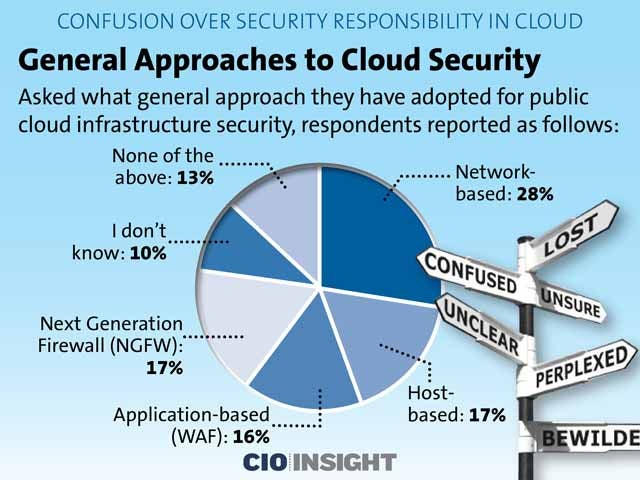 General Approaches to Cloud Security
General Approaches to Cloud Security
Asked what general approach they have adopted for public cloud infrastructure security, respondents reported as follows:
Network-based: 28%,
Host-based: 17%,
Application-based (WAF): 16%,
Next Generation Firewall (NGFW): 17%,
I don’t know: 10%,
None of the above: 13%
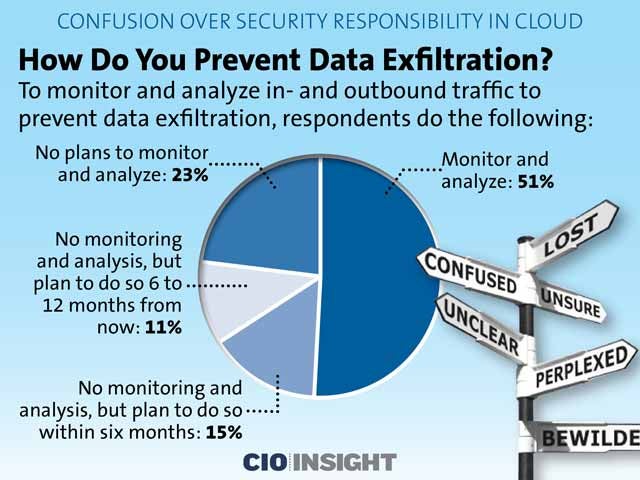 How Do You Prevent Data Exfiltration?
How Do You Prevent Data Exfiltration?
To monitor and analyze in- and outbound traffic to prevent data exfiltration, respondents do the following:
Monitor and analyze: 51%,
No monitoring and analysis, but plan to do so within six months: 15%,
No monitoring and analysis, but plan to do so 6 to 12 months from now: 11%,
No plans to monitor and analyze: 23%