
How to Ace Vendor Audits
 How to Ace Vendor Audits
How to Ace Vendor Audits
Few organizations purposely misuse assets, but many are caught out of compliance due to the increasing complexity of license usage policies.
 Highly Scrutinized
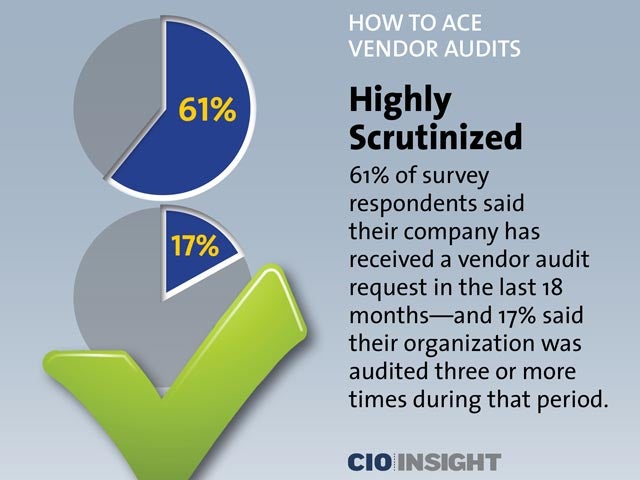
Highly Scrutinized
61% of survey respondents said their company has received a vendor audit request in the last 18 months—and 17% said their organization was audited three or more times during that period.
 Well Prepared but …
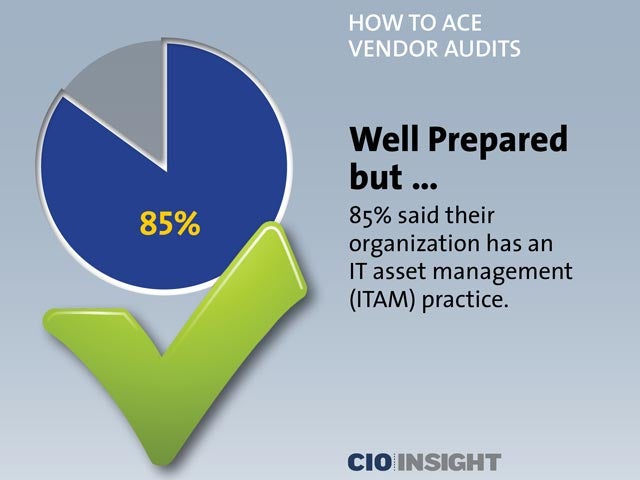
Well Prepared but …
85% said their organization has an IT asset management (ITAM) practice.
 … Under Equipped
… Under Equipped
Only 17% said they have ITAM tools in place to manage compliance in light of the audits.
 Bases Covered
Bases Covered
Nearly all companies with an ITAM practice use this data for service management, and 74% do so for vendor management.
 Above and Beyond
Above and Beyond
58% of organizations with an ITAM practice in place use this data for needs that go beyond standard ITAM functions, addressing functions such as security and architecture.
 Outdated Approach
Outdated Approach
57% of survey respondents said their company still “normalizes” its ITAM data manually.
 Best Practices for Navigating a Vendor Audit: Embrace Transparency
Best Practices for Navigating a Vendor Audit: Embrace Transparency
The best way to “get back to business as usual” is to be open about processes. Make the improvement of audit management issues part of your continuous improvement plan.
 Best Practices for Navigating a Vendor Audit: Ensure Security and Confidentiality of Data
Best Practices for Navigating a Vendor Audit: Ensure Security and Confidentiality of Data
While you may primarily focus on controlling audit activity and proving compliance, you shouldn’t overlook the need to control and manage the data being shared.
 Best Practices for Navigating a Vendor Audit: Beware of Phony Audit Requests
Best Practices for Navigating a Vendor Audit: Beware of Phony Audit Requests
Not all are legit. There are ill-intended vendors—often from foreign nations where your organization has an office—that will send bogus but authentic-looking requests when they’re actually just trying to sell something.