
How Malware Bypasses Detection Tools
 Web-Borne Malware Growing
Web-Borne Malware Growing
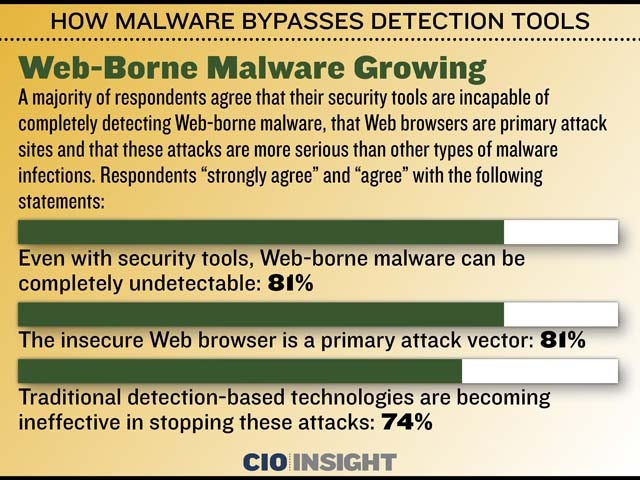
A majority of respondents agree that their security tools are incapable of completely detecting Web-borne malware, that Web browsers are primary attack sites and that these attacks are more serious than other types of malware infections. Respondents “strongly agree” and “agree” with the following statements: Even with security tools, Web-borne malware can be completely undetectable: 81%, The insecure Web browser is a primary attack vector: 81%, Traditional detection-based technologies are becoming ineffective in stopping these attacks: 74%
 Likelihood of Undetected Malware
Likelihood of Undetected Malware
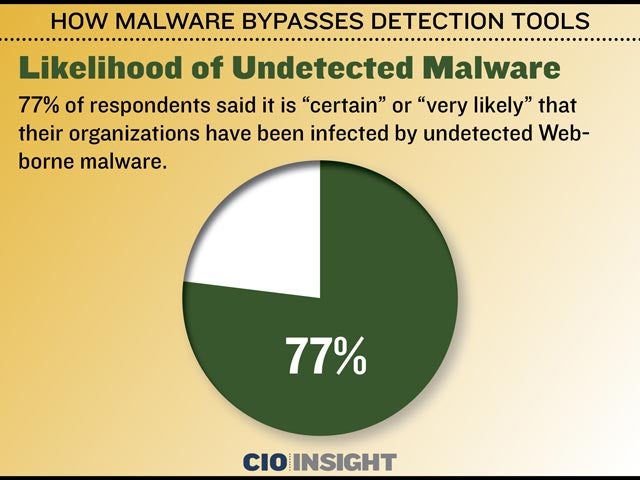
77% of respondents said it is “certain” or “very likely” that their organizations have been infected by undetected Web-borne malware.
 Budgets Hamper Malware Detection
Budgets Hamper Malware Detection
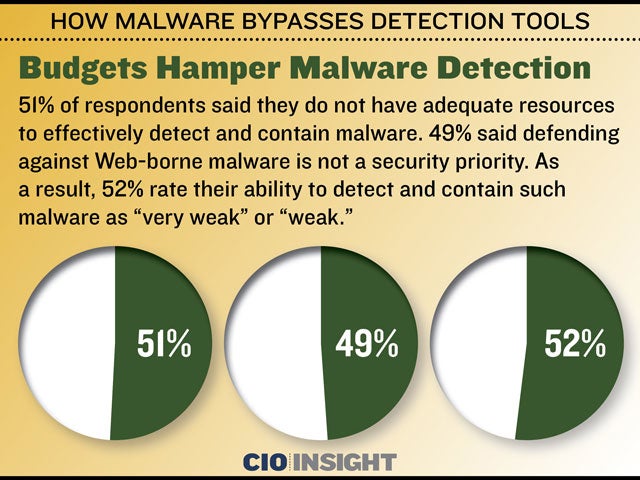
51% of respondents said they do not have adequate resources to effectively detect and contain malware. 49% said defending against Web-borne malware is not a security priority. As a result, 52% rate their ability to detect and contain such malware as “very weak” or “weak.”
 Impact of Unsecure Browsers
Impact of Unsecure Browsers
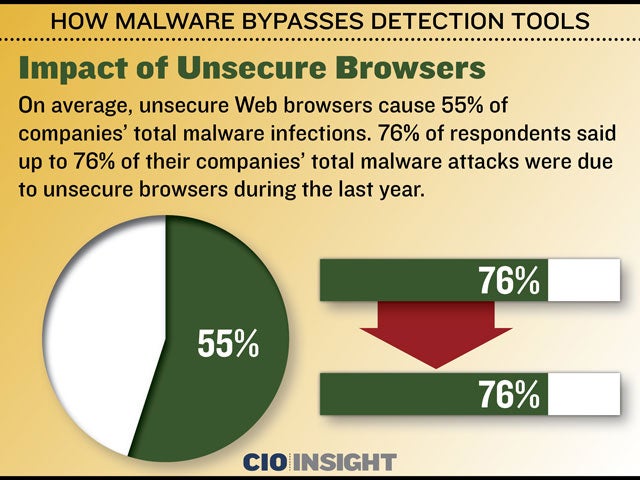
On average, unsecure Web browsers cause 55% of companies’ total malware infections. 76% of respondents said up to 76% of their companies’ total malware attacks were due to unsecure browsers during the last year.
 Sandboxes Help, but Not Enough
Sandboxes Help, but Not Enough
38% of respondents said Web-borne malware still penetrates sandboxes and content analysis engines.
 Other Defenses Bypassed
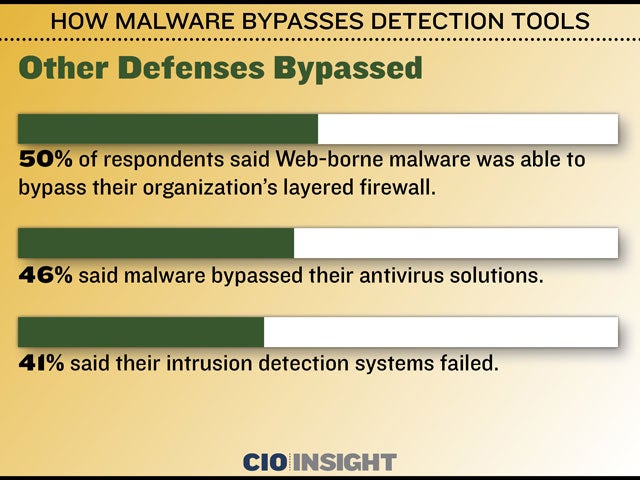
Other Defenses Bypassed
50% of respondents said Web-borne malware was able to bypass their organization’s layered firewall., 46% said malware bypassed their antivirus solutions., 41% said their intrusion detection systems failed.
 Putting a Price on Ending Malware
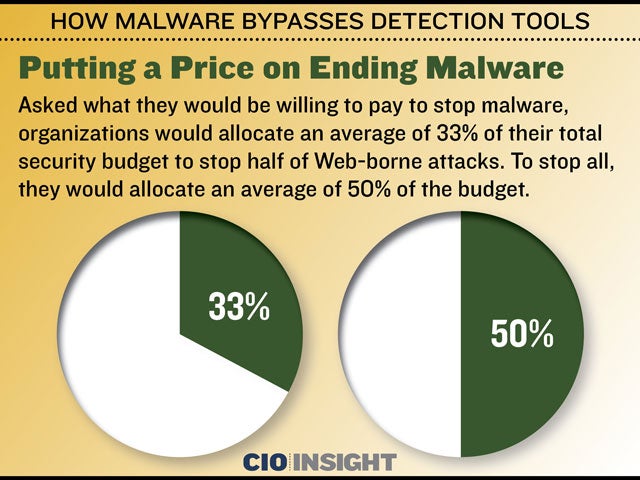
Putting a Price on Ending Malware
Asked what they would be willing to pay to stop malware, organizations would allocate an average of 33% of their total security budget to stop half of Web-borne attacks. To stop all, they would allocate an average of 50% of the budget.
 Containment Costs of Web-Borne Malware
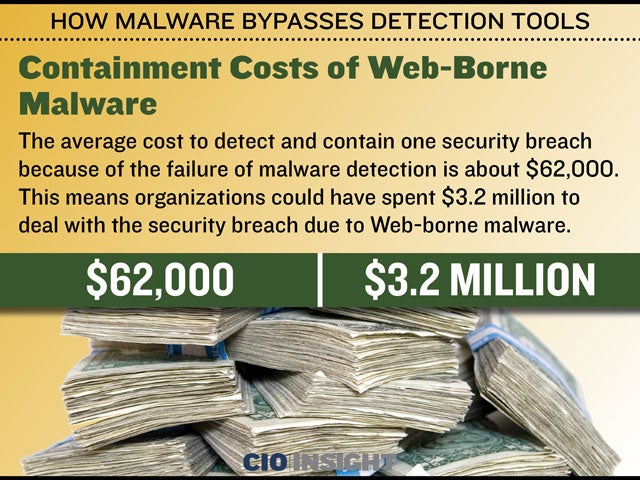
Containment Costs of Web-Borne Malware
The average cost to detect and contain one security breach because of the failure of malware detection is about $62,000. This means organizations could have spent $3.2 million to deal with the security breach due to Web-borne malware.
 Traditional Detection Is a Deterrent
Traditional Detection Is a Deterrent
Traditional methods deter organizations from adopting new solutions. 65% of respondents said overcoming psychological dependency on traditional detection methods would be a major barrier to adopting techniques that make traditional Web-borne malware detection and containment methods obsolete.