
Key Management a Barrier to Encryption Adoption
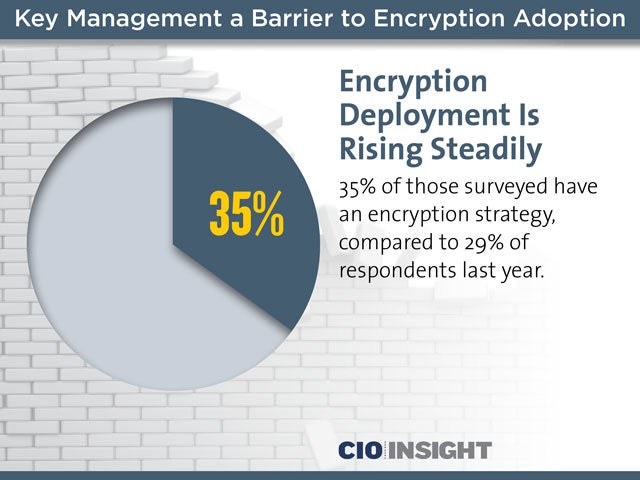 Encryption Deployment Is Rising Steadily
Encryption Deployment Is Rising Steadily
35% of those surveyed have an encryption strategy, compared to 29% of respondents last year.
 Top Driver For Encryption: Reducing Data Breaches
Top Driver For Encryption: Reducing Data Breaches
For the first time, the primary reason for deploying encryption is to reduce the impact of beaches, whereas previously it was to protect an organization’s brand or reputation.
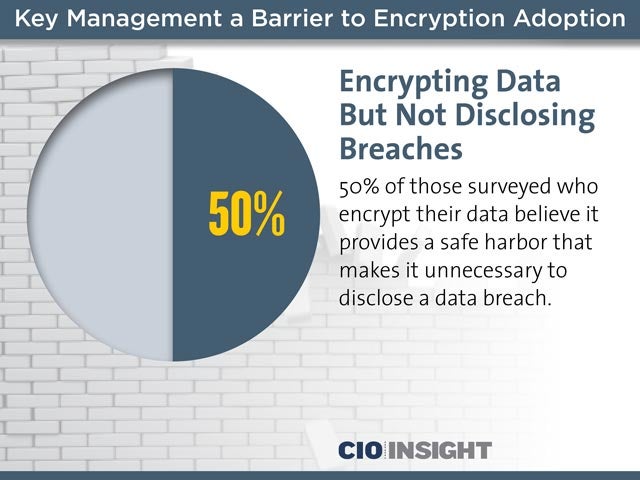 Encrypting Data But Not Disclosing Breaches
Encrypting Data But Not Disclosing Breaches
50% of those surveyed who encrypt their data believe it provides a safe harbor that makes it unnecessary to disclose a data breach.
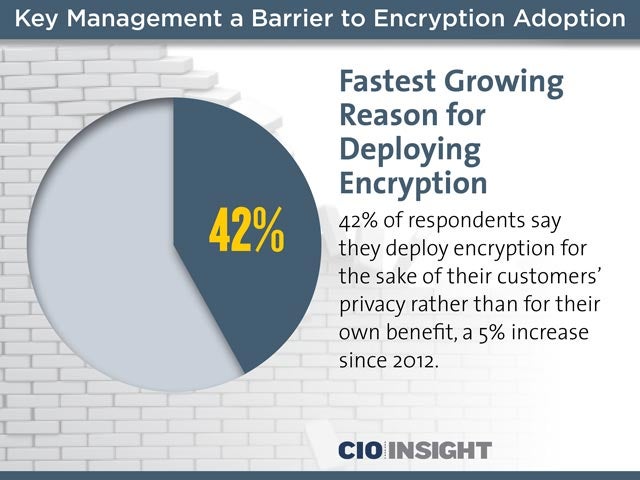 Fastest Growing Reason for Deploying Encryption
Fastest Growing Reason for Deploying Encryption
42% of respondents say they deploy encryption for the sake of their customers’ privacy rather than for their own benefit, a 5% increase since 2012.
 Top Threat Remains Mistakes by Employees
Top Threat Remains Mistakes by Employees
According to 27% of respondents, employee mistakes combined with system or process malfunctions result in concerns over inadvertent exposure. These factors outweigh concerns over malicious attacks by more than 2 to 1.
 Backup Tapes and Databases Most Need Encryption
Backup Tapes and Databases Most Need Encryption
Organizations ranked backup tapes and databases as the most important for encryption protection, followed by networks and laptops. Cloud encryption did not rank in the top 10.
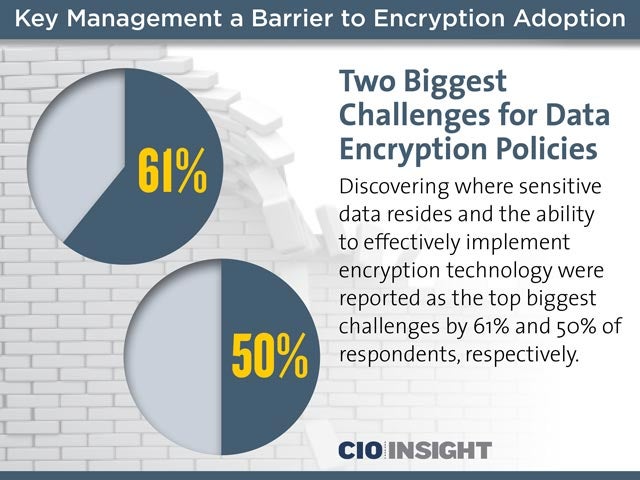 Two Biggest Challenges for Data Encryption Policies
Two Biggest Challenges for Data Encryption Policies
Discovering where sensitive data resides and the ability to effectively implement encryption technology were reported as the top biggest challenges by 61% and 50% of respondents, respectively.
 Key Management Remains a Major Issue
Key Management Remains a Major Issue
More than half of those surveyed rated the challenge of managing keys or certificates a 7 on a scale of 1 to 10. 30% of organizations rated key management at 9 or 10.
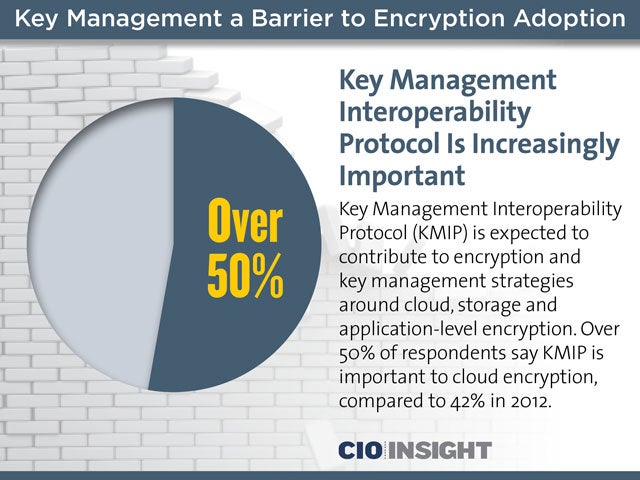 Key Management Interoperability Protocol Is Increasingly Important
Key Management Interoperability Protocol Is Increasingly Important
Key Management Interoperability Protocol (KMIP) is expected to contribute to encryption and key management strategies around cloud, storage and application-level encryption. Over 50% of respondents say KMIP is important to cloud encryption, compared to 42% in 2012.
 Hardware Security Modules Are Critical to Key Management
Hardware Security Modules Are Critical to Key Management
The report found that hardware security modules, devices to protect critical data processing activities and high-value keys, are increasingly considered a critical component of key management strategy.