
Known and Unknown Malware Continues to Grow
 Known and Unknown Malware Continues to Grow
Known and Unknown Malware Continues to Grow
A new study reveals 48 times more malware downloads this year compared to last year.
 Exponential Increase in Unknown Malware
Exponential Increase in Unknown Malware
Last year, 106 unknown malware variants hit an organization every hour. That’s 48 times more than the 2.2 downloads per hour reported in 2013.
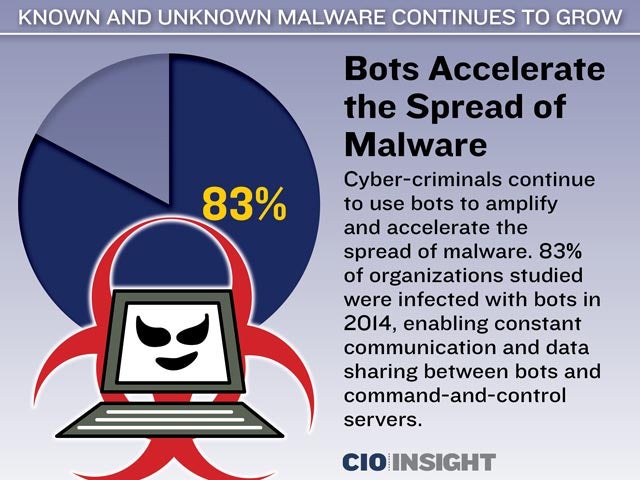 Bots Accelerate the Spread of Malware
Bots Accelerate the Spread of Malware
Cyber-criminals continue to use bots to amplify and accelerate the spread of malware. 83% of organizations studied were infected with bots in 2014, enabling constant communication and data sharing between bots and command-and-control servers.
 Mobile Devices Are the Biggest Vulnerability
Mobile Devices Are the Biggest Vulnerability
Mobile devices provide easier direct access to more valuable organizational assets than any other intrusion point.
 Probability of Infected Mobile Device
Probability of Infected Mobile Device
An organization that has more than 2,000 devices on its network has a 50% chance of at least six infected or targeted mobile devices on that network.
 Top Mobile Challenge: Securing Corporate Info
Top Mobile Challenge: Securing Corporate Info
72% of IT providers agree that their top mobile security challenge is to secure corporate information.
 Second Top Challenge: Personal Devices
Second Top Challenge: Personal Devices
67% of respondents said the second biggest challenge is managing personal devices that store both corporate and personal data.
 High Price of Risky Apps
High Price of Risky Apps
Applications become points of entry, rendering businesses vulnerable. Some, like file sharing, are obviously risky. The rise of shadow IT and applications that central IT does not sponsor or support have all led to even riskier business.
 Use of High-Risk Apps Is Rising
Use of High-Risk Apps Is Rising
96% of organizations studied used at least one high-risk application in 2014, a 10-point increase from 2013. 12.7 high-risk application events occur every hour.
 Data Loss Is a Top Concern
Data Loss Is a Top Concern
81% of participating organizations suffered a data loss incident, up 41% from 2013. While most security strategies focus on protecting data from hackers who enter from the outside, it’s equally important to protect data from the inside.