
Outdated Security Creates an IoT Danger
 Outdated Security Creates an IoT Danger
Outdated Security Creates an IoT Danger
Many companies are using outdated security methods to secure IoT devices, and they’re failing to include IoT in their security policies.
 Low Perceived IoT Penetration
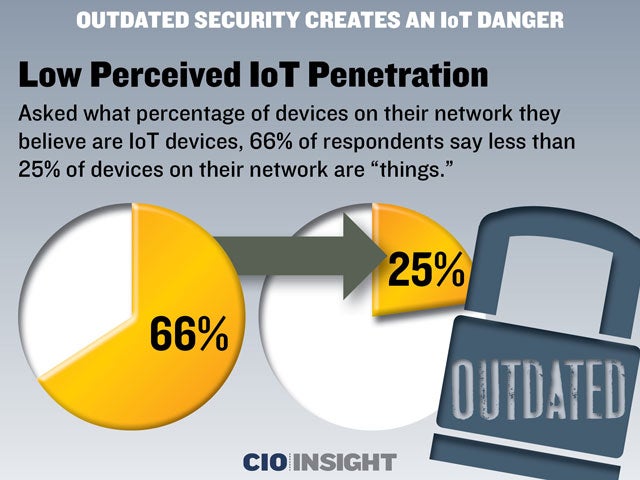
Low Perceived IoT Penetration
Asked what percentage of devices on their network they believe are IoT devices, 66% of respondents say less than 25% of devices on their network are “things.”
 Low Awareness of Networked Devices
Low Awareness of Networked Devices
85% of respondents are not confident that they are aware of all the devices on their network. Less than 33% are reasonably certain that they know about and can control all the things as soon as they are connected.
 Average Number of IoT Devices
Average Number of IoT Devices
Asked how many IoT devices they have on their network, respondents reported an average of nine IoT devices. 25% had five or fewer devices, and 62% had 6 to 15 devices.
 Respondents Who Reported No IoT Devices
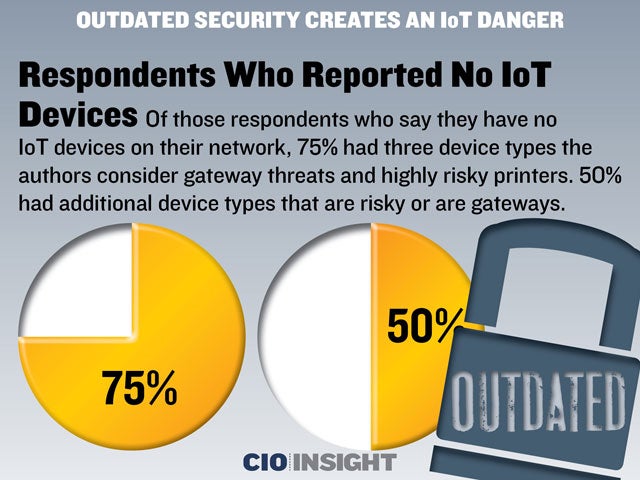
Respondents Who Reported No IoT Devices
Of those respondents who say they have no IoT devices on their network, 75% had three device types the authors consider gateway threats and highly risky printers. 50% had additional device types that are risky or are gateways.
 More on Respondents Who Reported No IoT Devices
More on Respondents Who Reported No IoT Devices
The average number of IoT devices among those who say they have none is eight, compared to those who recognize them, who reported having nine. So there is no significant difference in what is on the networks of the two categories of respondents.
 High Risk IoT Devices
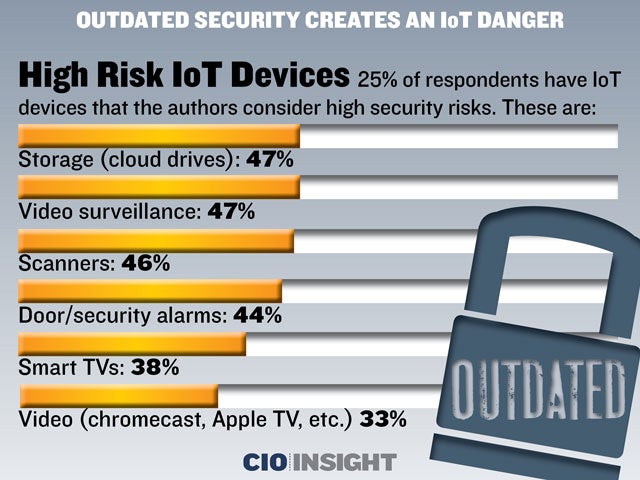
High Risk IoT Devices
25% of respondents have IoT devices that the authors consider high security risks. These are: Storage (cloud drives): 47%, Video surveillance: 47%, Scanners: 46%, Door/security alarms: 44%, Smart TVs: 38%, Video (chromecast, Apple TV, etc.) 33%
 IoT Devices and Security Policy
IoT Devices and Security Policy
Asked whether their company has a security policy for IoT devices, 44% of respondents said yes, but 25% did not know whether their security policy includes these devices.
 Security Policy and Home Networks
Security Policy and Home Networks
33% of respondents’ companies have policies that include home networks, which is troublesome because the “intelligent home” is one of the first widespread IoT implementations.
 Importance of Discovery and Classification
Importance of Discovery and Classification
Asked how important it is to discover an IoT device on their network, 89% of respondents say it is important. Asked how important it is to classify the type of device, 87% think it is important.
 Importance of Discovery and Classification Without an Agent
Importance of Discovery and Classification Without an Agent
86% of respondents think it is important to discover/classify IoT devices without using an agent.
 Most Methods of Securing IoT Devices Ineffective
Most Methods of Securing IoT Devices Ineffective
Respondents are using traditional security methods designed for intelligent computing devices that are ineffective for Things; 50% use passwords and similar security. Only 19% use specialized agents to monitor their network. 25% either don’t know, or know that they use nothing.
 Two Biggest Challenges For IoT Security
Two Biggest Challenges For IoT Security
41% of respondents say IT and OT functions working together is the biggest challenge for IoT security. The next most chosen challenge is acknowledging IoT devices, according to 34% of respondents.