
Addressing the Growing IoT Risks to the Enterprise
 Addressing the Growing IoT Risks to the Enterprise
Addressing the Growing IoT Risks to the Enterprise
Many organizations aren’t keeping up with key IoT security requirements, and hackers are increasingly planting backdoors to launch automated IoT botnet attacks.
 Risk Rises
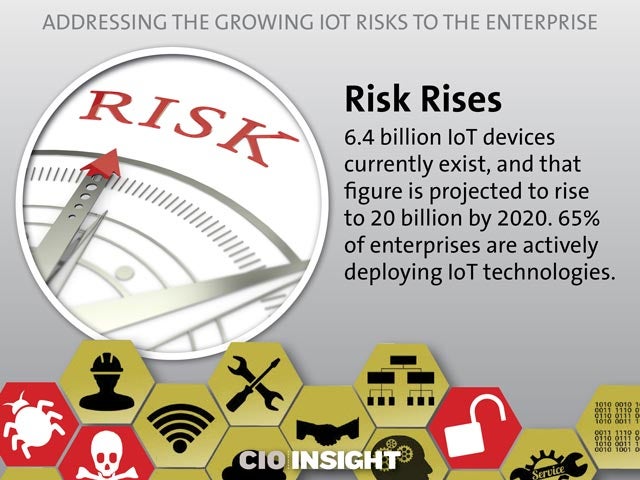
Risk Rises
6.4 billion IoT devices currently exist, and that figure is projected to rise to 20 billion by 2020. 65% of enterprises are actively deploying IoT technologies.
 Risk #1: IP-Connected Security Systems
Risk #1: IP-Connected Security Systems
Many security systems use proprietary RF technology that lacks authentication and encryption. Many also fail to use frequency hopping, which protects against jamming and spoofing.
 Risk #2: IP-Connected Infrastructure
Risk #2: IP-Connected Infrastructure
HVAC systems typically operate on the same network as internal systems. Thus, hackers can intercept data, escalate privilege and carry out attacks. They can also manipulate controls.
 Risk #3: Connected Printers
Risk #3: Connected Printers
Without physical access, hackers can compromise printers to siphon their private documents. They also can gain administrative control of the printer.
 Risk #4: VoIP Phones
Risk #4: VoIP Phones
These devices can be subject to remote snooping and, in some cases, the speakerphone can be switched on without the knowledge of the user.
 Risk #5: Smart Appliances
Risk #5: Smart Appliances
Lax certificate checking and other vulnerabilities open the door to a man-in-the-middle attack to intercept communications and modify traffic between a client and server.
 Risk #6: Smart Lightbulbs
Risk #6: Smart Lightbulbs
These devices, which rely on mesh networks, can be sniffed by attackers. They can extract password-protected WiFi credentials and other data.
 How an Attack Unfolds
How an Attack Unfolds
Attackers can use the internet—as well as wireless communication protocols like WiFi, Bluetooth and ZigBee—to spread an infection. Any network within wireless range is susceptible.
 Best Practices
Best Practices
Discover and classify all devices at the time they are connected
Control network access based on device type and behavior
Integrate islands of security and leverage existing investments
 Final Thoughts
Final Thoughts
Security teams should consider a comprehensive and agentless approach that delivers real-time visibility into devices, while eliminating the need for constant re-deployment of security controls.