
Company Memo: We Can’t Protect Consumer Data
 Company Memo: We Can’t Protect Consumer Data
Company Memo: We Can’t Protect Consumer Data
To avoid a public-relations nightmare, companies rely on privacy risk assessments and audits and invest in security awareness training sessions for staff.
 Risk Factor
Risk Factor
Less than one-third of survey respondents are “very” confident in their enterprise’s ability to ensure the privacy of its sensitive data.
 Broken Trust
Broken Trust
More than half do not think consumers today should feel confident that enterprises are adequately protecting their personal information (PI).
 Top Negative Consequences of a Privacy Breach
Top Negative Consequences of a Privacy Breach
Reputation decline: 80%, Legal action: 62%, Regulatory action: 60%. Unfavorable press coverage: 58%
 Report Card
Report Card
Two-thirds said the primary metric to measure their company’s effectiveness on privacy governance is the number of breaches/incidents experienced, while nearly half cite the number of privacy complaints received from customers/clients.
 Best Practices, Part 1
Best Practices, Part 1
75% said their organization’s use of privacy policies, procedures, standards and other management approaches is mandatory, while 19% indicate this is “recommended.”
 Best Practices, Part II
Best Practices, Part II
46% said their company will perform a privacy risk assessment to monitor the effectiveness of its privacy program, while about two out of five said their organization will perform a privacy self-assessment and/or undergo a privacy audit.
 Designated Duty
Designated Duty
Nine out of 10 said their organization has assigned someone to be accountable for privacy, with the Chief Information Security Officer or Chief Security Officer most likely to oversee this (within 23% of companies).
 School in Session
School in Session
76% said their company provides privacy awareness training to staff.
 Top Certifications Held by Privacy Management/Staff
Top Certifications Held by Privacy Management/Staff
Certified Information Systems Auditor (CISA): 51%, Certified Information Systems Security Professional (CISSP): 36%, Certified Information Security Manager: (CISM): 34%
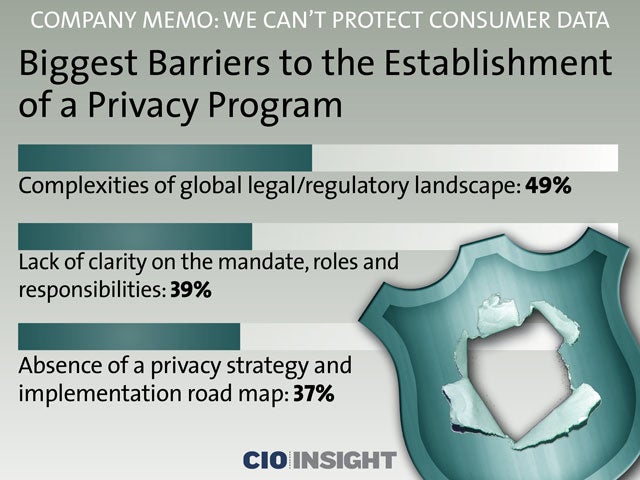 Biggest Barriers to the Establishment of a Privacy Program
Biggest Barriers to the Establishment of a Privacy Program
Complexities of global legal/regulatory landscape: 49%, Lack of clarity on the mandate, roles and responsibilities: 39%, Absence of a privacy strategy and implementation road map: 37%