
How Fake ‘Insiders’ Can Hijack an Organization
 How Fake ‘Insiders’ Can Hijack an Organization
How Fake ‘Insiders’ Can Hijack an Organization
Cyber-attackers posing as legitimate insiders with privileged accounts are at the core of most cyber-attacks, yet many IT leaders are unaware of the danger.
 Top Concern: Stolen Admin, Privileged Accounts
Top Concern: Stolen Admin, Privileged Accounts
38% of respondents said stolen administrative and privileged credentials are their No. 1 security concern. 27% cited phishing attacks. 23% cited malware on the network and 12% cited infected endpoints.
 Most Difficult Stage to Mitigate
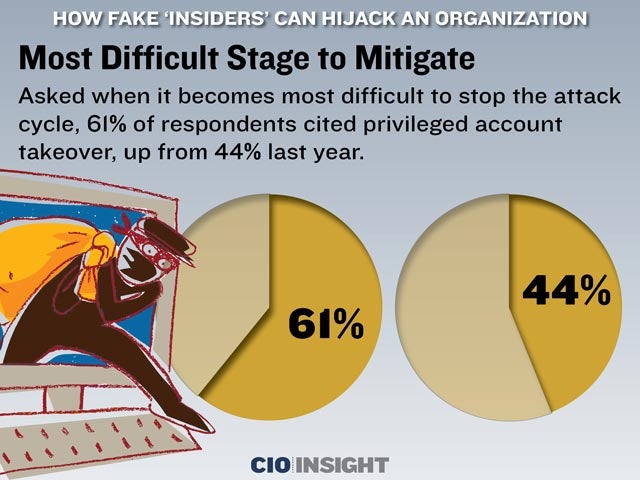
Most Difficult Stage to Mitigate
Asked when it becomes most difficult to stop the attack cycle, 61% of respondents cited privileged account takeover, up from 44% last year.
 Time to Discover Breach
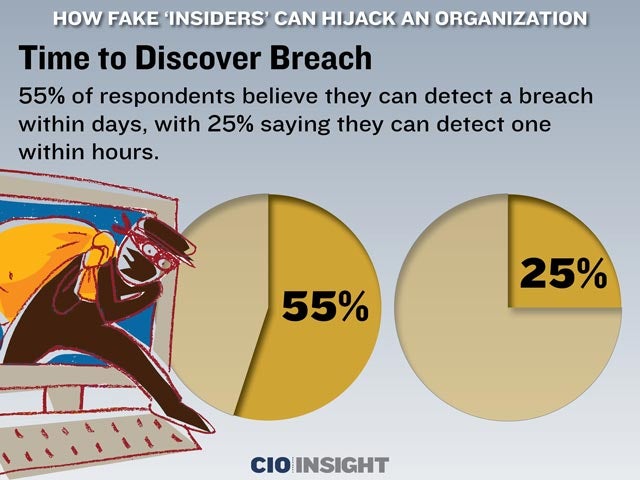
Time to Discover Breach
55% of respondents believe they can detect a breach within days, with 25% saying they can detect one within hours.
 Types of Attacks of Greatest Concern
Types of Attacks of Greatest Concern
The types of attacks respondents are most concerned about are: Password Hijacking: 72%, Phishing Attacks: 70%, SSH (secure shell) Key Hijacking: 41%, Pass-the-Hash: 36%, Golden Ticket: 23%
 Confidence in Cyber-Strategy
Confidence in Cyber-Strategy
57% of respondents said they are confident in their organization’s CEO and/or boards ability to provide sound leadership regarding security strategy.
 Confidence in Preventing Network Breaches
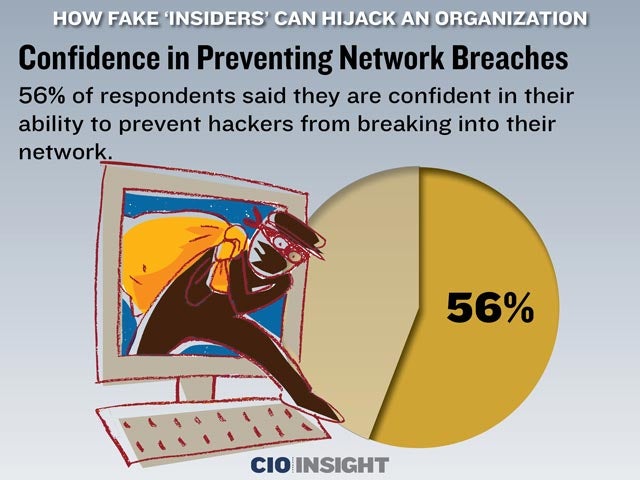
Confidence in Preventing Network Breaches
56% of respondents said they are confident in their ability to prevent hackers from breaking into their network.
 Leading Factors Responsible for Most Beaches
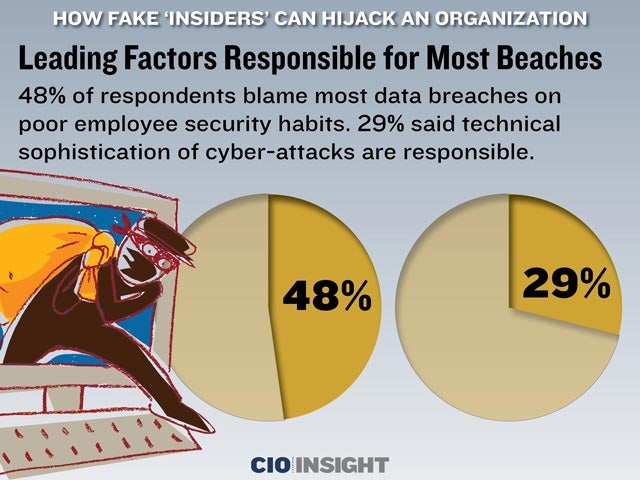
Leading Factors Responsible for Most Beaches
48% of respondents blame most data breaches on poor employee security habits. 29% said technical sophistication of cyber-attacks are responsible.
 Automated Privileged Account Management
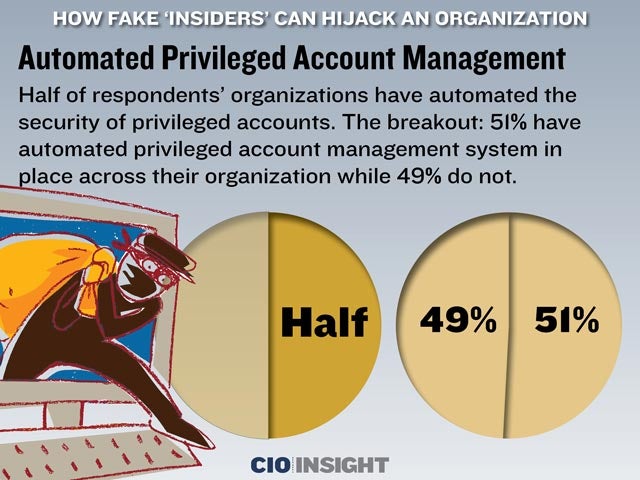
Automated Privileged Account Management
Half of respondents’ organizations have automated the security of privileged accounts. The breakout: 51% have automated privileged account management system in place across their organization while 49% do not.
 Is Compliance Sufficient to Prevent Breaches?
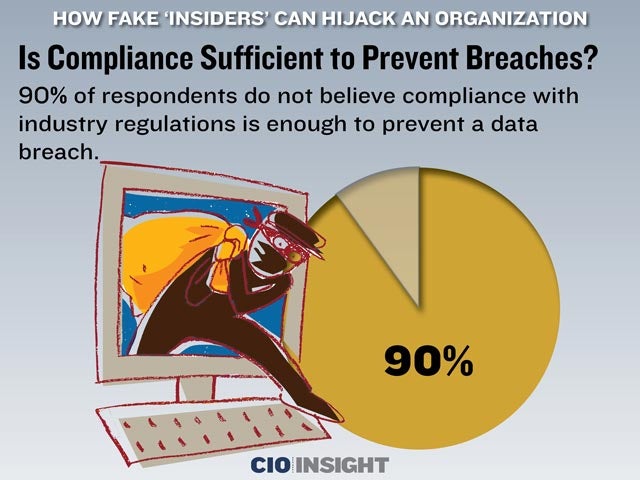
Is Compliance Sufficient to Prevent Breaches?
90% of respondents do not believe compliance with industry regulations is enough to prevent a data breach.