
Mature Access Management Curtails Breaches
 Mature Access Management Curtails Breaches
Mature Access Management Curtails Breaches
Enterprise security is woefully inadequate, but it could benefit from more comprehensive and mature identity and access management.
 Majority Experienced Five Breaches Since 2015
Majority Experienced Five Breaches Since 2015
66% of the IT security decision-makers surveyed experienced an average of five or more security breaches during the past two years
 Most Organizations Have Immature IAMs
Most Organizations Have Immature IAMs
83% of the organizations surveyed don’t have a mature approach to IAM.
 IAM Maturity Hierarchy
IAM Maturity Hierarchy
28% of the respondents had Level 1 IAM maturity, 30% were Level 2, 25% were Level 3 and 17% were Level 4.
 IAM Maturity Is Linked to Fewer Security Incidents
IAM Maturity Is Linked to Fewer Security Incidents
There is a correlation between implementing more IAM capabilities (especially adopting best practices with regard to privileged identity management) and a reduction in security incidents.
 Most Mature Firms Have Half As Many Breaches
Most Mature Firms Have Half As Many Breaches
Level I companies experience an average of 12.5 breaches compared to Level 4 firms, which only experience 5.7.
 How Six Key Areas Are Affected by Maturity Level
How Six Key Areas Are Affected by Maturity Level
49% of Level 4 firms (compared with only 32% of Level 1 firms) are likely to never experience a breach across six key areas: networks, servers, on-premises apps, databases, cloud apps for SaaS, and cloud apps for IaaS and PaaS.
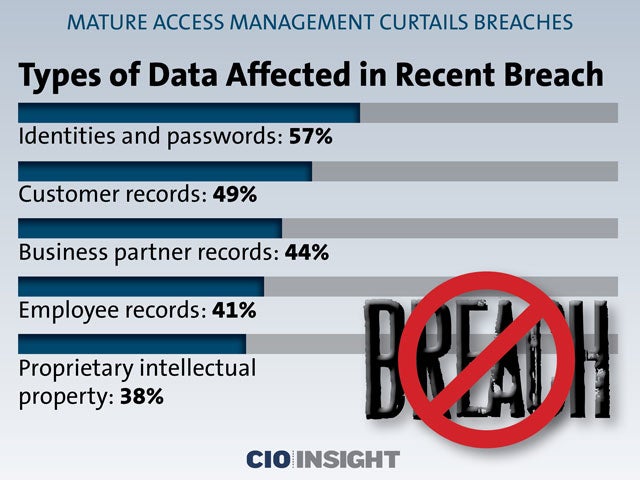 Types of Data Affected in Recent Breach
Types of Data Affected in Recent Breach
Identities and passwords: 57%,
Customer records: 49%,
Business partner records: 44%,
Employee records: 41%,
Proprietary intellectual property: 38%
 Characteristics of Level 4 Firms
Characteristics of Level 4 Firms
91% use an integrated IAM platform.
They save 40% on AIM technology costs.
They average $5 million in cost savings.
51% have improved user productivity.