
Nine Things You Need to Know About Insider Threats
 Types of Incidents
Types of Incidents
35% of organizations have experienced at least one insider threat, with the following breakdown (the total does not equal 100% as some respondents had more than one type of incident): Data leak: 49%, Fraud : 41%, Data breach: 36%, IP theft: 16%
 Who Discovers Insider Threats
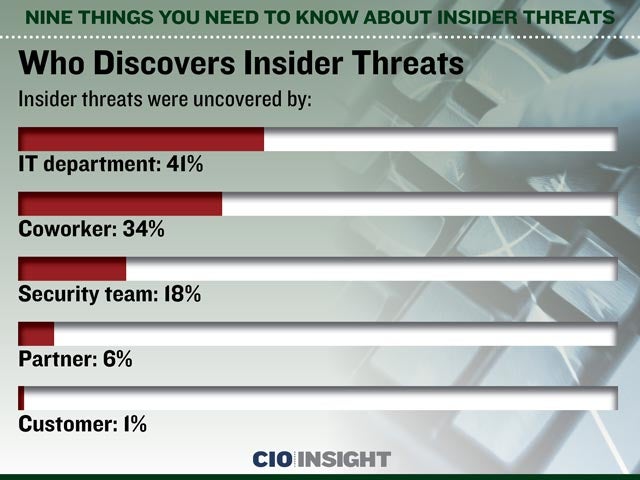
Who Discovers Insider Threats
Insider threats were uncovered by: IT department: 41%, Coworker: 34%, Security team: 18%, Partner: 6%, Customer: 1%
 Average Financial Impact
Average Financial Impact
Losses from insider threats most-often cost less than $50,000: 70% of respondents report financial losses of under $50,000, 17% suffered losses of $50,000 to $100,000, 6% lost $100,000 to $500,000, 4% lost $500,000 to $1 million, 3% lost over $1 million
 Reasons for Lack of Preparedness
Reasons for Lack of Preparedness
61% of organizations say they are not prepared for insider threats (the total exceeds 100% as multiple factors could be cited): Lack of training: 55%, Inadequate budget: 51%, Low priority: 34%, Understaffed: 34%, Lack of technology: 31%
 Prevention Is a Challenge
Prevention Is a Challenge
Even though 49% of respondents say they are trying to detect insider threats, 59% of these respondents admit that they cannot detect them.
 Detection Is Harder Than Deterrence or Detailing
Detection Is Harder Than Deterrence or Detailing
42% say detection is harder than deterrence or detailing an attack. Why? Because it’s more straightforward. It’s more about technology than psychology.
 What You Can Do About Deterrence
What You Can Do About Deterrence
SpectorSoft recommends drafting and implementing an acceptable use policy that spells out what is and is not acceptable for employees. It also puts them on notice that the organization has the right to monitor activity on company-provided devices and on the company network.
 What You Can Do About Detection
What You Can Do About Detection
Talk to security experts and make a list of types of monitoring that best fit your organization. Implement solutions that you can customize and extend to meet changing needs.
 What You Can Do About Details
What You Can Do About Details
There are products specially designed to investigate the details of an attack. Choose one that can help you limit the damage and remove the source of the threat.