
Security Breaches Just a Matter of Time
 Victims of a Security Breach
Victims of a Security Breach
Many businesses have experienced a security breach or expect one to occur., Just over half either admit or are aware their security has been breached: 53%, Admit employees have seen documents they shouldn’t: 52%, Admit it is “just a matter of time” before another security breach occurs: 51%
 The Importance of IAM
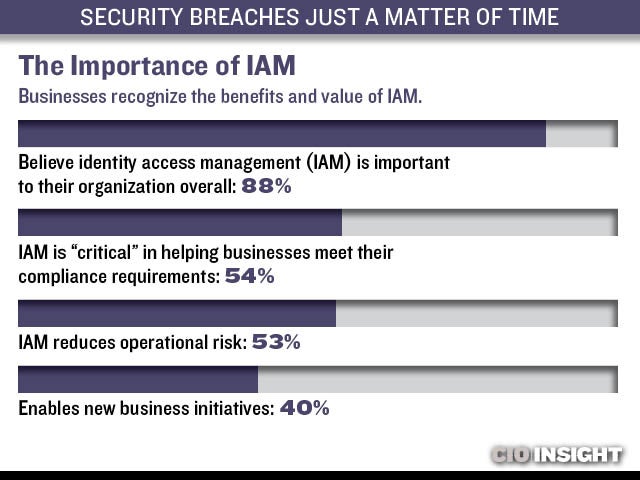
The Importance of IAM
Businesses recognize the benefits and value of IAM. Believe identity access management (IAM) is important to their organization overall: 88%, IAM is “critical” in helping businesses meet their compliance requirements: 54%, IAM reduces operational risk: 53%, Enables new business initiatives: 40%
 Primary Focus of IAM Strategy
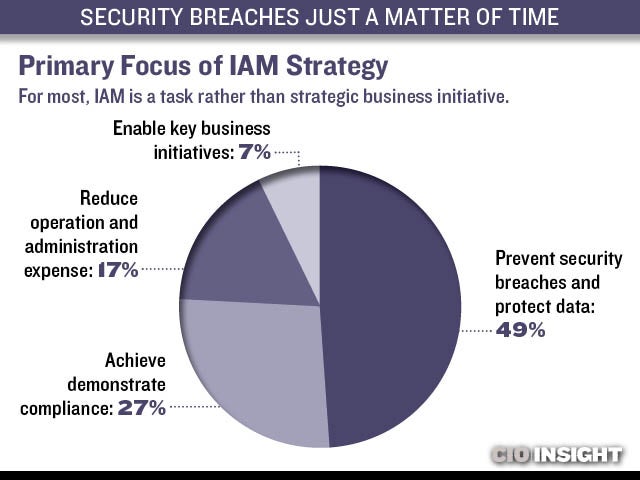
Primary Focus of IAM Strategy
For most, IAM is a task rather than strategic business initiative. Prevent security breaches and protect data: 49%, Achieve demonstrate compliance: 27%, Reduce operation and administration expense: 17%, Enable key business initiatives: 7%
 IAM Challenges
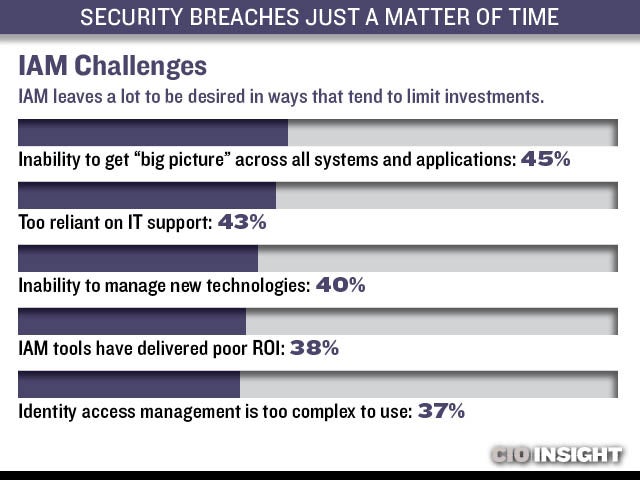
IAM Challenges
IAM leaves a lot to be desired in ways that tend to limit investments. Inability to get “big picture” across all systems and applications: 45%, Too reliant on IT support: 43%, Inability to manage new technologies: 40%, IAM tools have delivered poor ROI: 38%, Identity access management is too complex to use: 37%
 Confidence in Granting or Revoking Employee Access
Confidence in Granting or Revoking Employee Access
Just more than half say they are very confident in their access control mechanisms. Very confident: 54%, Somewhat confident: 35%, Not particularly confident: 10%, Not at all confident: 1%
 The Mobile Computing Challenge
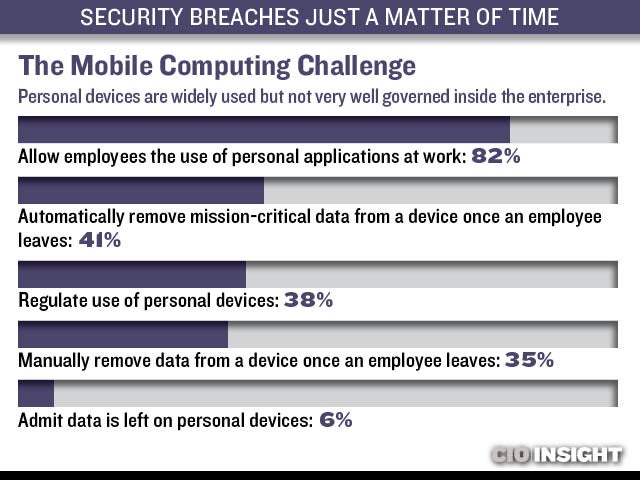
The Mobile Computing Challenge
Personal devices are widely used but not very well governed inside the enterprise. Allow employees the use of personal applications at work: 82%, Automatically remove mission-critical data from a device once an employee leaves: 41%, Regulate use of personal devices: 38%, Manually remove data from a device once an employee leaves: 35%, Admit data is left on personal devices: 6%
 Cloud Application Mandates
Cloud Application Mandates
Despite cloud mandates, most IAM systems don’t extend policies to software-as-a-service applications. Such a policy is already in place: 63%, No, but expect policy in next two years: 25%, No, but expect policy in next 12 months: 10%, No, but expect one beyond two years: 2%
 Percentage of Mission-Critical Applications in the Cloud
Percentage of Mission-Critical Applications in the Cloud
The cloud is rapidly becoming more strategic. Currently in the cloud: 39%, Expect to be in the cloud by 2016: 59%