
When False Positives Waste Tech Team’s Time
 When False Positives Waste Tech Team’s Time
When False Positives Waste Tech Team’s Time
As organizations struggle to enact a strategy that helps detect and prevent security threats, too many false positives burn up time and energy in IT departments.
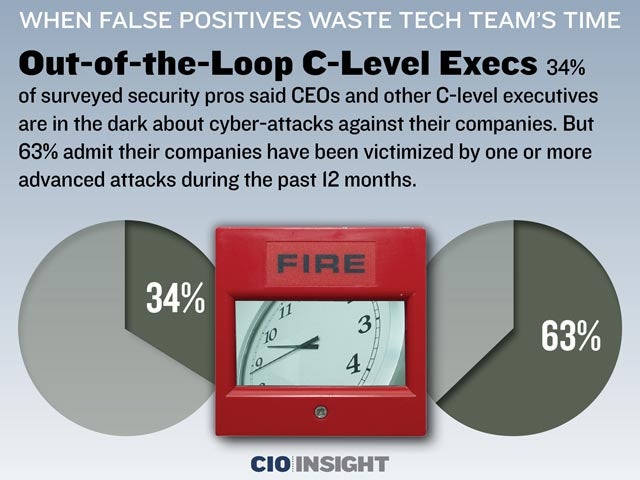 Out-of-the-Loop C-Level Execs
Out-of-the-Loop C-Level Execs
34% of surveyed security pros said CEOs and other C-level executives are in the dark about cyber-attacks against their companies. But 63% admit their companies have been victimized by one or more advanced attacks during the past 12 months.
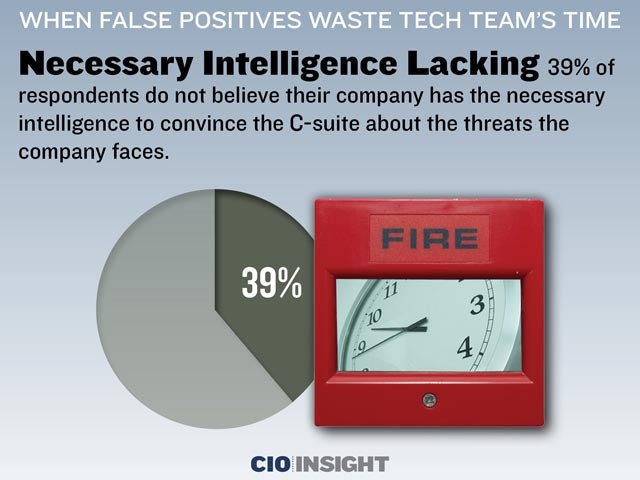 Necessary Intelligence Lacking
Necessary Intelligence Lacking
39% of respondents do not believe their company has the necessary intelligence to convince the C-suite about the threats the company faces.
 Some Slow to Detect Attacks
Some Slow to Detect Attacks
21% of respondents say they took between 1-2 years to detect an attack. 21% took from 1-6 months to contain the breach.
 Others Discover Attacks Within Hours
Others Discover Attacks Within Hours
30% of companies discovered an attack between 1-8 hours after it occurred. 28% contained a breach in 1-8 hours.
 Malware Remains a Challenge
Malware Remains a Challenge
68% of respondents say their security team spends a significant amount of time chasing false positives of malware attacks.
 More About False Positives
More About False Positives
On average, 29% of all malware alerts are investigated and on average 40% are false positives. Only 18% of respondents say their malware detection tool tells them the risk level for each incident.
 Wide Range of Security Budget Expectations
Wide Range of Security Budget Expectations
The average cyber-security budget is $16 million, 34% of which will be allocated to incident response efforts. 50% of respondents say their budget will remain the same, 37% are expected to increase, and 13% expect it to decrease this year.
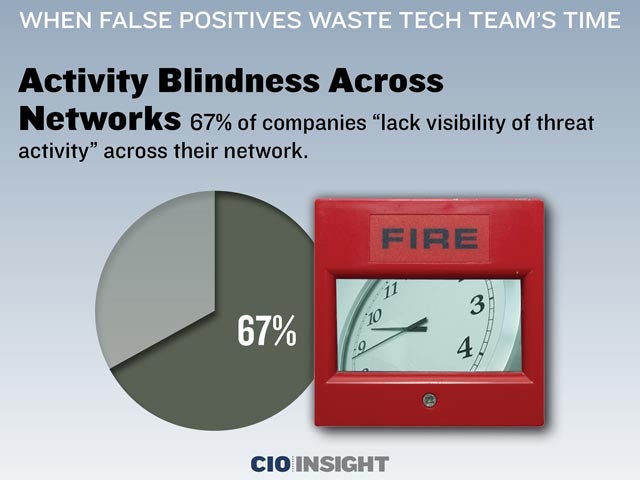 Activity Blindness Across Networks
Activity Blindness Across Networks
67% of companies “lack visibility of threat activity” across their network.
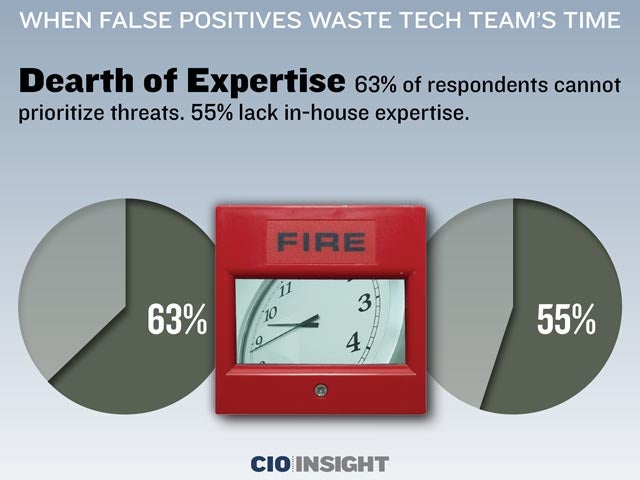 Dearth of Expertise
Dearth of Expertise
63% of respondents cannot prioritize threats. 55% lack in-house expertise.
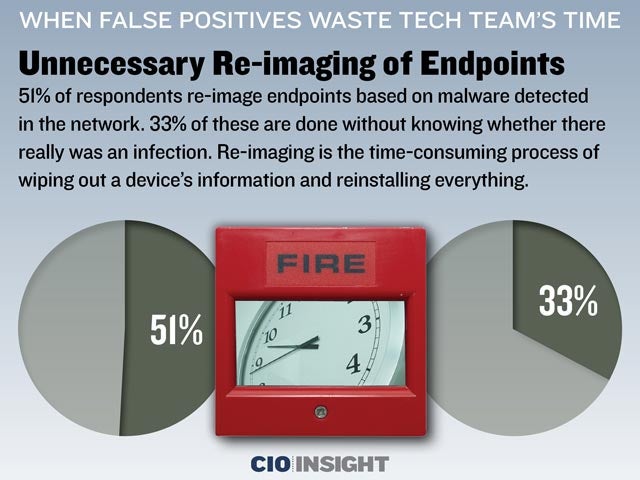 Unnecessary Re-imaging of Endpoints
Unnecessary Re-imaging of Endpoints
51% of respondents re-image endpoints based on malware detected in the network. 33% of these are done without knowing whether there really was an infection. Re-imaging is the time-consuming process of wiping out a device’s information and reinstalling everything.