
Why Security Execs Lack Confidence in Security
 Why Security Execs Lack Confidence in Security
Why Security Execs Lack Confidence in Security
IT security pros need to consider metrics such as dwell time, or reducing the time a threat is in a network, which helps strengthen overall security posture.
 Executives Are Tentative About Security Posture
Executives Are Tentative About Security Posture
31% of respondents are still very confident about their security posture, but 65% are only somewhat confident.
 Communication Over Security Posture
Communication Over Security Posture
28% of respondents said the security metrics they use to communicate are effective whereas 65% said the metrics are only somewhat effective.
 Where Is the Disconnect?
Where Is the Disconnect?
Executives rely on quantitative metrics while breaches occur.
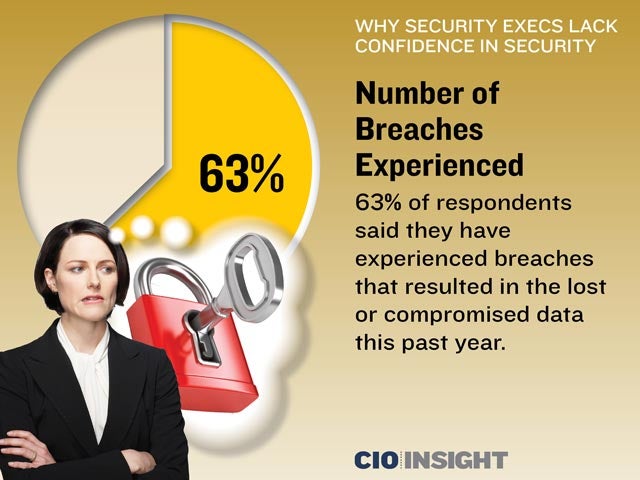 Number of Breaches Experienced
Number of Breaches Experienced
63% of respondents said they have experienced breaches that resulted in the lost or compromised data this past year.
 Why Executives Are Not Confident About Security
Why Executives Are Not Confident About Security
Executives are not confident about their security posture because of the way they measure it; most count alerts and incidents, which does not shed light on the real security posture.
 Quantitative Metrics Won’t Help
Quantitative Metrics Won’t Help
“Using quantitative metrics—like counting breaches, totaling response times, and calculating downtime—does not help when breaches are a constant,” the report states.
 Metrics Used
Metrics Used
Rather than measure dwell time, more organizations measure cost of incidents (39%) and reduction in vulnerabilities (39%). These are not as important as how long the threat, attacker or attack vector exists inside an organization and actions taken once past defenses.
 The Importance of Dwell Time
The Importance of Dwell Time
Only 33% of those surveyed measure dwell time, the elapsed time from initial breach to containment. If you limit the time a threat exists, damage to the enterprise will be minimized.
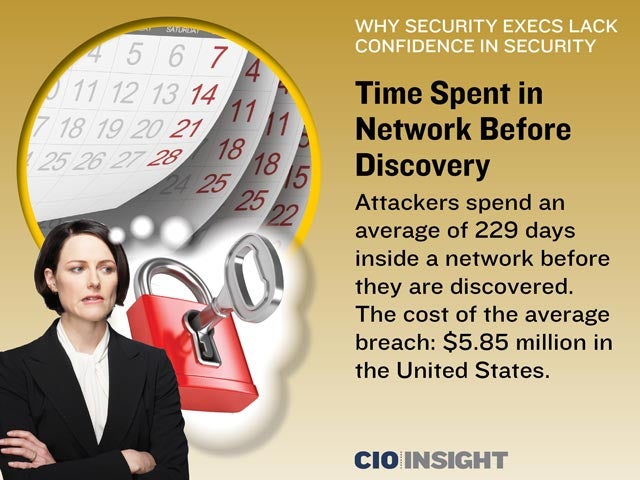 Time Spent in Network Before Discovery
Time Spent in Network Before Discovery
Attackers spend an average of 229 days inside a network before they are discovered. The cost of the average breach: $5.85 million in the United States.
 Recommendation
Recommendation
Reduce the time a malicious threat acts from within. This will greatly reduce potential damage, speed of mitigation and contain exposure.