
As cyber attacks become increasingly common and sophisticated the importance of threat intelligence cannot be understated.
Threat intelligence feeds in particular are digital tools that aggregate data to indicate emerging and existing security threats in real time, according to your company’s key metrics. That way you can effectively sort out the most important and imminent threats.
Feeds are a simple way to start building out your company’s threat intelligence capabilities and assessing your threat posture. It serves as a first line of defense that detects outside threats with an internal security system that will alert security analysts according to targeted areas of interest.
You can configure the feed to leverage your cyber intelligence by setting up automatic alerts and/or integrating it with your security information and event management (SIEM) platform.
More robust threat intelligence feeds, however, will utilize machine learning on their own to automatically gather, process, and analyze incoming data from internal sources, such as logs and records, as well as external sources, such as the open web or dark web, in order to generate actionable insights.
Read more: Best Threat Intelligence Platforms & Tools for 2021
Best Threat Intelligence Feeds
There are free, open-source threat intelligence feeds out there, but those may not provide the specific information your company needs. Moreover, other market comparisons focus on criteria that all of the below vendors share, such as integrations, analytics, alerts, and reporting.
Below, however, we consider threat intelligence feed vendors according to key differentiating factors: predictive analytics, AI/ML, and natural language processing.
Analytics | ||||
|---|---|---|---|---|
Cofense Intelligence
The Cofense Intelligence suite contains various tools that use automated, AI-based techniques to analyze millions of messages daily from a variety of web sources. It specializes in preventing phishing scams and other security threats to your network, such as malware attacks. Cofense Intelligence delivers both alerts and actionable insights that are highly customizable.
Cofense Intelligence operates with several of the big names in the SecOps landscape, so it will feed directly into your SIEM, TIP, SOAR tools, and more, so you can detect and guard against threats early on.
Crowdstrike’s Falcon X
Crowdstrike’s Falcon X threat intelligence software provides automatic analysis and context based on a list of indicators of compromise (IoCs) tailored to your specific company. In fact, you can easily visualize your IoCs with a graph that shows the relationships among them. Based on user reviews, you’ll likely find Falcon X’s interface intuitive and easy to integrate with your own security solution.
But depending on how robust your current tools are, you may get even more value out of Falcon X Premium or Falcon X Elite. While Falcon X focuses on threat scanning and alerts, Falcon X Premium and Elite offer up further intelligence and an assigned intelligence analyst from Crowdstrike (available with Elite).
Dataminr Pulse
Dataminr Pulse is a threat intelligence feed designed to be scaled and customized for businesses of various sizes and industries. With the Hub feature in Dataminr Pulse, you get an overview of your geographical locations and their level of security. As your business grows, you can easily add and manage more locations in the Hub.
Dataminr is also highly customizable. You can tailor security alerts and create dashboards based on various issues, levels of criticality, and geographical locations. Regardless of the metrics you use to customize your alerts, Dataminr Pulse Employs AI and mines public data (more than 200,000 sources, from 100+ languages) to produce real-time alerts, as well as visual and geographical context.
Dataminr has many facets to its threat intelligence software, but can be parsed down to avoid scope creep and fit what your company needs. Users frequently mention its ease of use and integration into their company’s own security workflow, as well as the depth and breadth of knowledge and support that Dataminr provides.
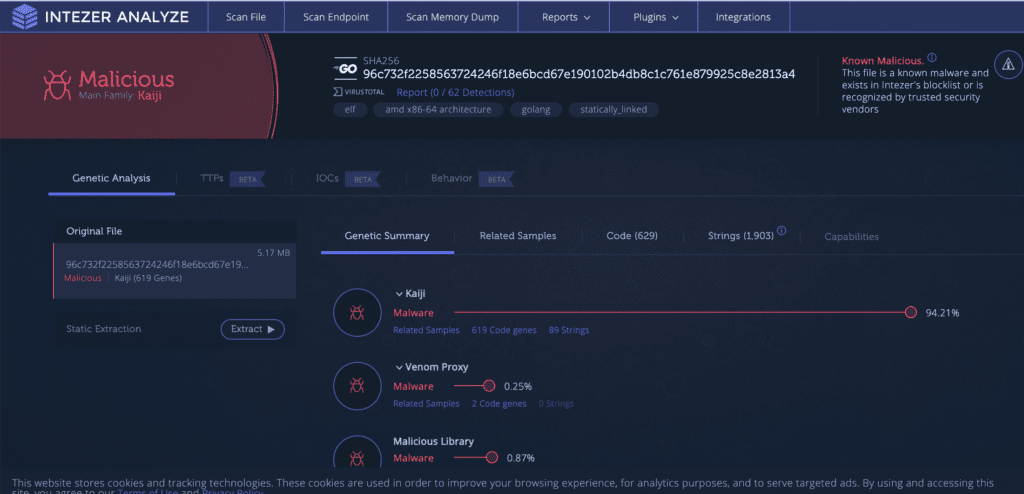
Intezer Analyze
Intezer Analyze is an all-in-one malware analysis platform that includes threat alerting and intelligence. It integrates with mainstream tools, such as Cortex XSOAR, Fortinet, Maltego, and Splunk. Users have noted integration issues, however, so check beforehand to ensure that Intezer Analyze is compatible with the SOC tools that you’re currently using.
Intezer Analyze conducts deep code analysis to compare new iterations of malware code to previous versions in order to quickly identify malware threats and alert users. It’s designed with various audiences in mind, with easy-to-understand reporting.
Recorded Future
Recorded Future’s platform includes its threat intelligence solution, which features predictive, actionable intelligence in real time. Planned attacks can take place in any language, but Recorded Future operates in multiple languages. It uses natural language processing to assign meta-tags to unstructured data that it gathers from around the world.
The data that Recorded Future aggregates is delivered through a variety of channels: web portal, mobile app, or browser extension. It provides context and assigns risk scores for potential threats in a way that’s not only intelligible to various stakeholders — from security novices to experts — but also takes the guesswork out of prioritizing risks.
Recorded Future also employs machine learning to build rich data sets, from which it offers up predictive analytics, so you remain proactive in addressing security threats.
Resecurity Context
Resecurity Context is a cyber threat intelligence platform that includes a portal for managing internal and external threat intelligence feeds. It allows you to configure your own alerts according to topic and how you want to be notified, whether via email or SMS.
Once you configure your alerts and notification preferences, Context casts a wide source net. For example, it draws from over 300 million dark web data entries, as well as unstructured data from over 40 languages. After initial preference setting and data collection, Context then processes, analyzes, reports, and evaluates, as part of its six-step cycle.
Webroot BrightCloud
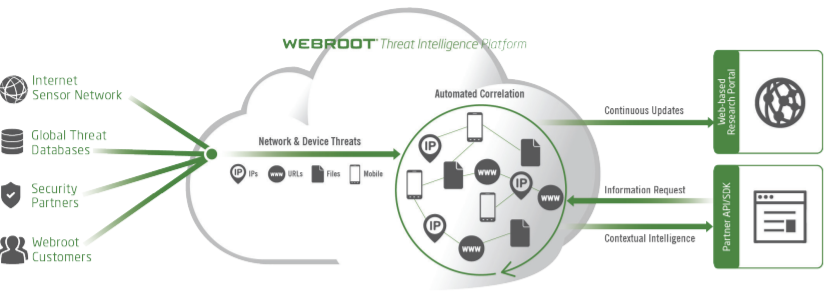
Popular among SMBs, Webroot BrightCloud Threat Intelligence is a low-commitment collection of SaaS that integrates seamlessly with apps and browsers you use on a daily basis. It automatically runs scheduled scans on billions of URLs and IP addresses to ensure peace of mind at both the network and endpoint levels.
In fact, that’s what most users report: ease of use and not needing to worry about being protected as they open emails and surf the web. Webroot BrightCloud employs machine learning to classify and organize IP addresses and URLs according to its level of threat to your business. BrightCloud encompasses six different services to address your company’s particular needs.
How to Choose a Threat Intelligence Feed
Know Your Enemies
Think through your intelligence goals first. What specific threats do you want your threat intelligence feed to be on the lookout for? If you’re looking for a specific solution, like phishing, Cofense Intelligence, is a great place to start. If malware is your focus, check out Intezer Analyze.
Read more: Top Cyber Security Threats to Organizations
The Importance of AI for Threat Intelligence
All threat intelligence feeds employ some form of artificial intelligence to the extent that they perform automatic scans to pick up on and analyze IoCs. Only some of the vendors listed here (Falcon X, Recorded Future, Resecurity, and Webroot) deploy machine learning for generating actionable insights and predictive analytics, which is key for staying ahead of the curve on emerging threats.
Moreover, some of the vendors use machine learning for natural language processing capabilities, such as Recorded Future and Resecurity. This is a standout feature that warrants more attention, given that bad actors plan and carry out attacks from around the world in various languages, and can target any organization regardless of its size and geographical reach.
Feed Compatibility
Integration is a standard benefit of threat intelligence feeds on the market today. To get the most out of your feed, integrate it with your company’s existing security management solution and security workflows, but ensure compatibility with your particular solutions beforehand.
Feed Customization
Take advantage of the level of customization available in your feed of choice to fit your company’s use case(s). This will allow the feed to generate the most relevant data and insights. If your company already employs a suite of security tools, your intelligence goals are likely more targeted, which will require a feed that allows for customization, such as Cofense Intelligence, Falcon X, or Dataminr Pulse.
In terms of notification variety, Recorded Future is an outlier, as it is the only one to specifically mention functionality on the web, in a mobile app, and as a browser extension.
Keep Audience in Mind
Keep in mind who is accessing the feed and their level of technical knowledge. If various stakeholders are using the feed, make sure there are corresponding levels of granularity for people with technical expertise, as opposed to management-level staff.
If user-friendly analytics and reporting is a high-ranking criterion in your selection process, start by checking out Falcon X, Dataminr Pulse, Intezer Analyze, or Recorded Future.
Choosing the Right Threat Intelligence Feed
Each of the vendors here has something to offer in terms of level of specificity, scalability, and capability. Recorded Future is the all-around winner, based on its fulfillment of the three criteria of predictive analytics, natural language processing, and AI/ML capabilities, but there is no magic-bullet solution for every organization.