
Why Insider Threats Are Inevitable
 Why Insider Threats Are Inevitable
Why Insider Threats Are Inevitable
Insider threats have risen significantly during the last year, with the greatest threat coming from privileged users such as managers, contractors and consultants.
 Who Are the Insiders?
Who Are the Insiders?
Managers pose the greatest insider threat, at 59%, according to respondents, followed by contractors and consultants (48%) and regular employees (46%).
 Few Have Appropriate Controls
Few Have Appropriate Controls
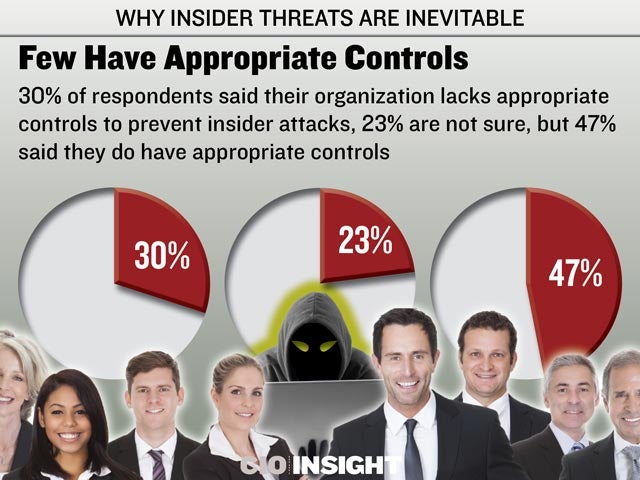
30% of respondents said their organization lacks appropriate controls to prevent insider attacks, 23% are not sure, but 47% said they do have appropriate controls
 Costs of Data Breaches
Costs of Data Breaches
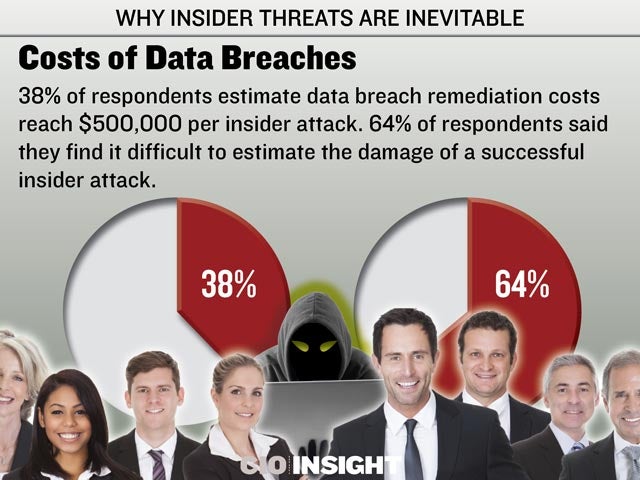
38% of respondents estimate data breach remediation costs reach $500,000 per insider attack. 64% of respondents said they find it difficult to estimate the damage of a successful insider attack.
 Top Insider Threat
Top Insider Threat
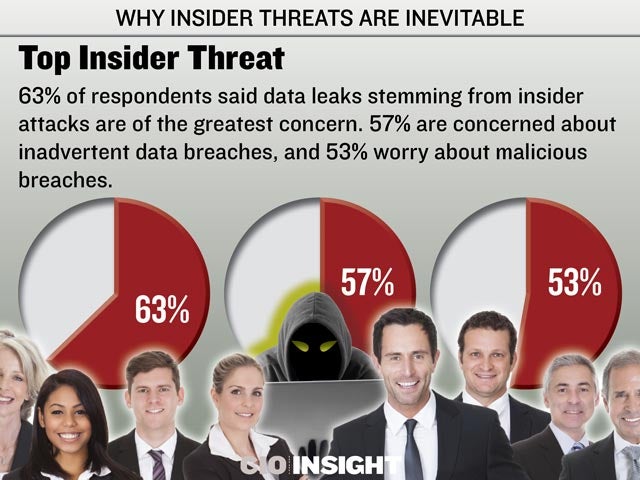
63% of respondents said data leaks stemming from insider attacks are of the greatest concern. 57% are concerned about inadvertent data breaches, and 53% worry about malicious breaches.
 IT Assets at Risk
IT Assets at Risk
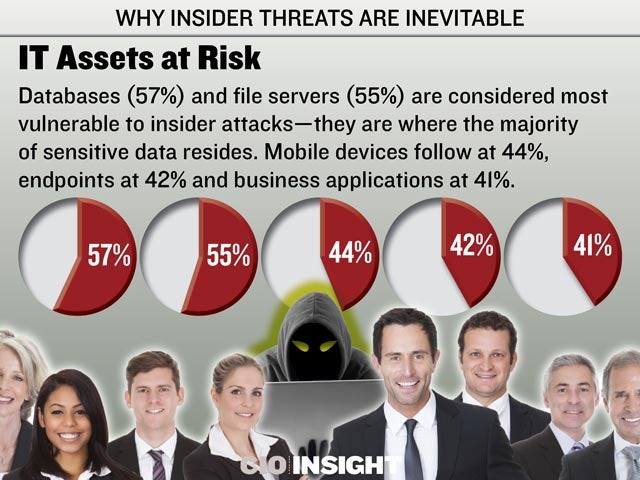
Databases (57%) and file servers (55%) are considered most vulnerable to insider attacks—they are where the majority of sensitive data resides. Mobile devices follow at 44%, endpoints at 42% and business applications at 41%.
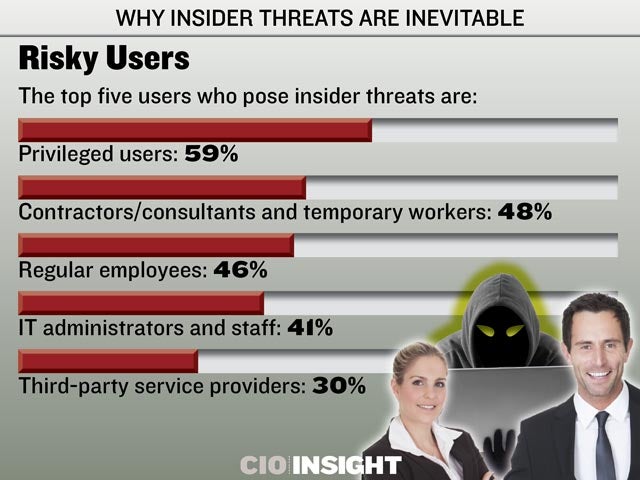 Risky Users
Risky Users
The top five users who pose insider threats are: Privileged users: 59%, Contractors/consultants and temporary workers: 48%, Regular employees: 46%, IT administrators and staff: 41%, Third-party service providers: 30%
 Most Vulnerable Apps
Most Vulnerable Apps
The top five most vulnerable types of apps are: Collaboration and communication: 45%, Cloud storage and file sharing: 43%, Finance and accounting: 38%, Social media: 33%, Sales and marketing: 29%
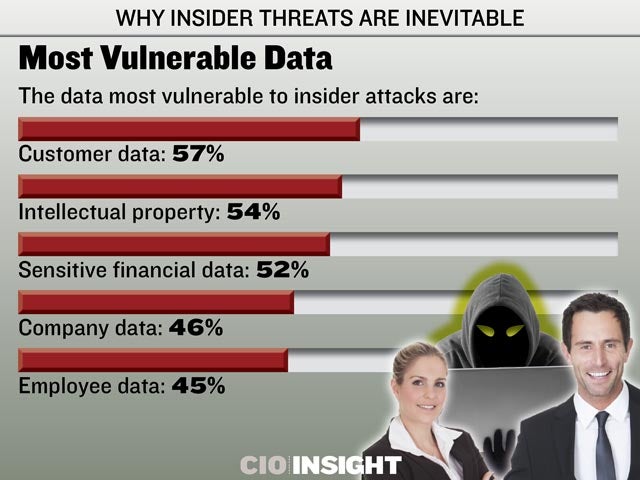 Most Vulnerable Data
Most Vulnerable Data
The data most vulnerable to insider attacks are: Customer data: 57%, Intellectual property: 54% ,Sensitive financial data: 52% ,Company data: 46%, Employee data: 45%
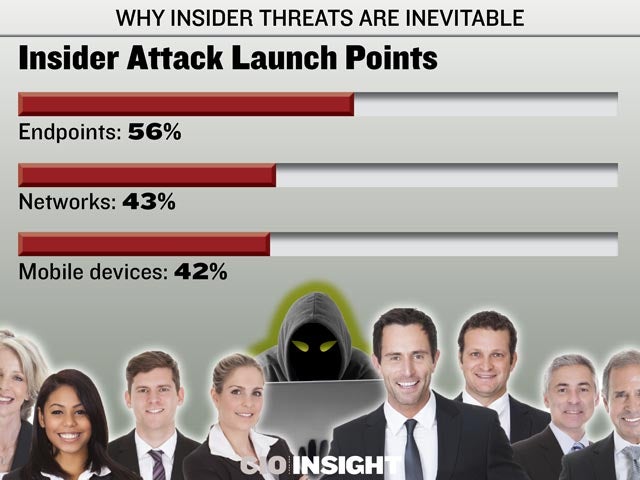 Insider Attack Launch Points
Insider Attack Launch Points
Endpoints: 56%, Networks: 43%, Mobile devices: 42%
 Internal vs External Attacks
Internal vs External Attacks
62% of respondents said insider attacks are harder to detect and prevent than external attacks. The key reasons: insiders often already have access to systems and sensitive information (66%), increased use of cloud-based apps (58%) and the rise in the amount of data leaving the protected network (42%).
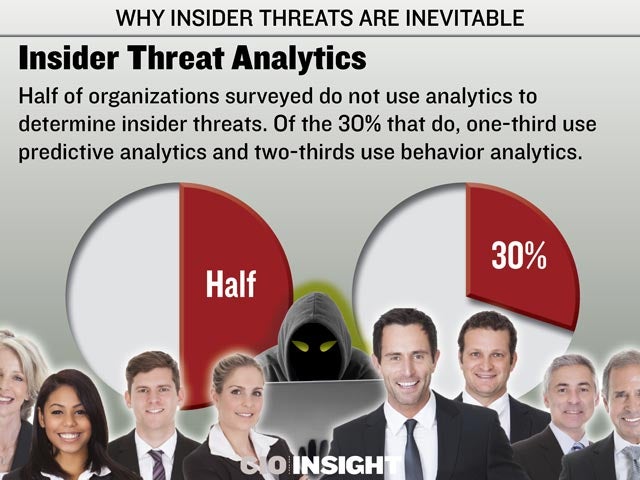 Insider Threat Analytics
Insider Threat Analytics
Half of organizations surveyed do not use analytics to determine insider threats. Of the 30% that do, one-third use predictive analytics and two-thirds use behavior analytics.
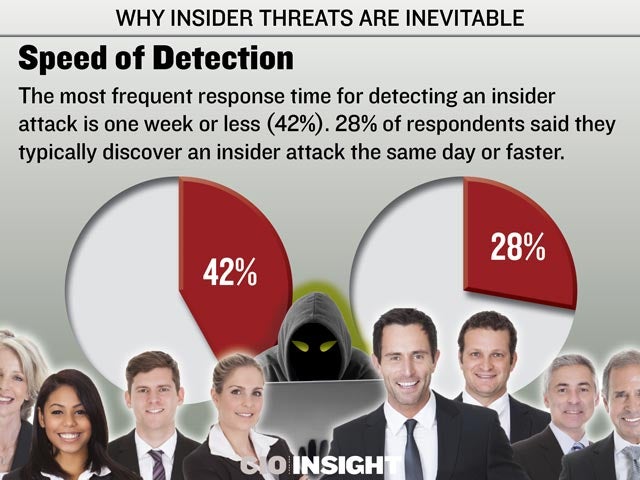 Speed of Detection
Speed of Detection
The most frequent response time for detecting an insider attack is one week or less (42%). 28% of respondents said they typically discover an insider attack the same day or faster.