
Mounting Security Threats Boost the Status of CIOs
 Mounting Security Threats Boost the Status of CIOs
Mounting Security Threats Boost the Status of CIOs
CEOs consider CIOs among the most important C-level executives, saying that these IT leaders play an important role in bringing security to board-level thinking.
 IT Security Is a Top Priority
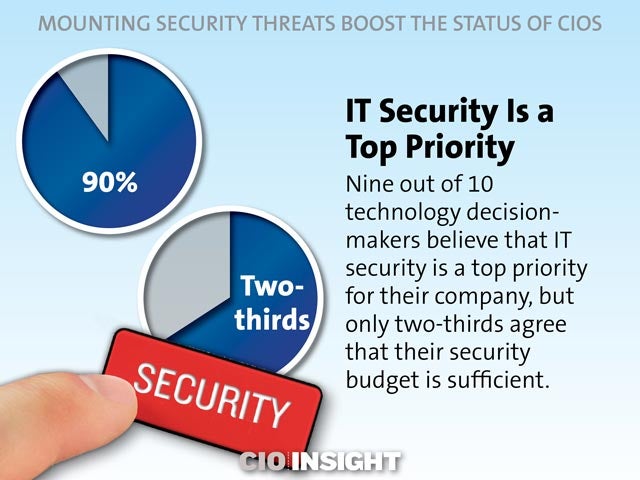
IT Security Is a Top Priority
Nine out of 10 technology decision-makers believe that IT security is a top priority for their company, but only two-thirds agree that their security budget is sufficient.
 Cloud Security Spending Increased
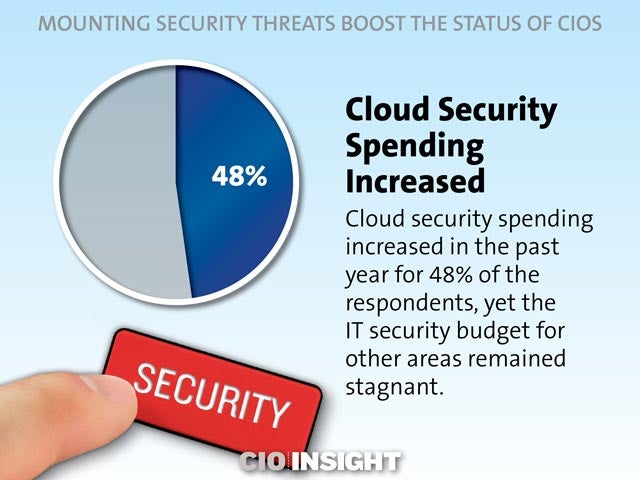
Cloud Security Spending Increased
Cloud security spending increased in the past year for 48% of the respondents, yet the IT security budget for other areas remained stagnant.
 Resources Don’t Prevent All Attacks
Resources Don’t Prevent All Attacks
Only 64% of cyber-attacks can be stopped, detected or prevented with current resources, according to the survey respondents.
 Wondering How Breaches Occurred
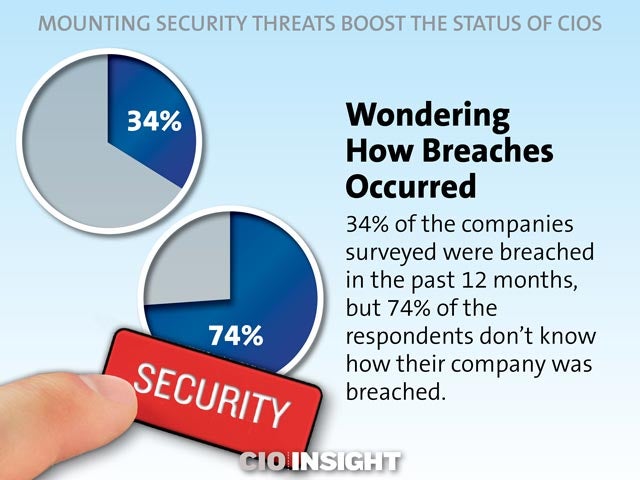
Wondering How Breaches Occurred
34% of the companies surveyed were breached in the past 12 months, but 74% of the respondents don’t know how their company was breached.
 Paying to Avoid a Public Scandal
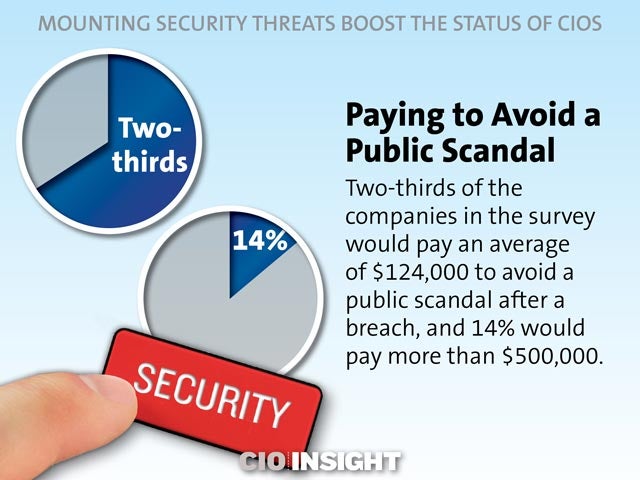
Paying to Avoid a Public Scandal
Two-thirds of the companies in the survey would pay an average of $124,000 to avoid a public scandal after a breach, and 14% would pay more than $500,000.
 CIOs’ Importance to the Company
CIOs’ Importance to the Company
My job is more important in the company’s hierarchy: 34%,
My job has completely transformed in past years: 30%,
My job is as important as it used to be: 36%
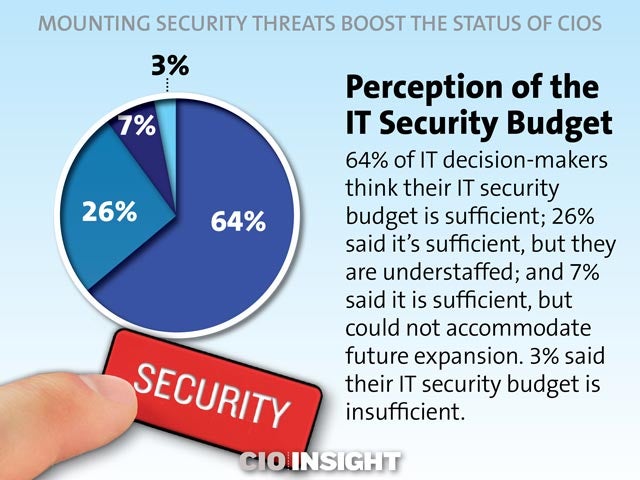 Perception of the IT Security Budget
Perception of the IT Security Budget
64% of IT decision-makers think their IT security budget is sufficient; 26% said it’s sufficient, but they are understaffed; and 7% said it is sufficient, but could not accommodate future expansion. 3% said their IT security budget is insufficient.
 How to Make Your Data Secure, Part I
How to Make Your Data Secure, Part I
Define criteria for storing on-premises or in-cloud data.
Perform risk management.
Keep your cloud private.
Be aware of geographical jurisdiction and data-handling laws.
Perform due diligence on a cloud service provider.
Stipulate damages.
 How to Make Your Data Secure, Part II
How to Make Your Data Secure, Part II
Encrypt data locally and in transit.
Back up cloud data.
Use secure, multiple authentication mechanisms.
Limit employee access to sensitive data.
Prevent DDoS attacks.
Create, define and implement security response procedures.