
Risk Is IT’s Problem No Matter What
 Risk Is IT’s Problem No Matter What
Risk Is IT’s Problem No Matter What
A survey says that risks created by departments beyond IT are still its responsibility, therefore, enterprises should focus on identity governance.
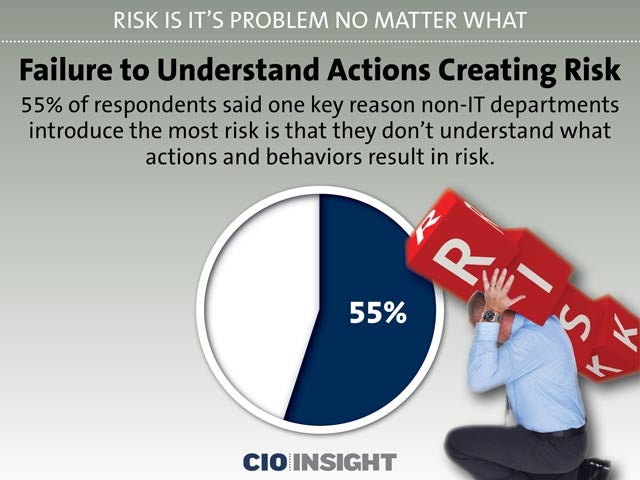 Failure to Understand Actions Creating Risk
Failure to Understand Actions Creating Risk
55% of respondents said one key reason non-IT departments introduce the most risk is that they don’t understand what actions and behaviors result in risk.
 Latest Applications Adopted Without Formal Policies
Latest Applications Adopted Without Formal Policies
71% of organizations surveyed have embraced BYOD and SaaS, but less than half have implemented formal policies to protect corporate data.
 Disconnect Between Policy And Enforcement
Disconnect Between Policy And Enforcement
33% of respondents said their users do not follow policy and 72% of respondents are concerned about BYOD and shadow IT as exposure points.
 Identity Governance Key to Managing Risk
Identity Governance Key to Managing Risk
71% of respondents said their organization’s data would be less exposed if they were better equipped to manage it. 71% of respondents whose organization has introduced identity governance solutions believe they will result in a more automated and efficient organization.
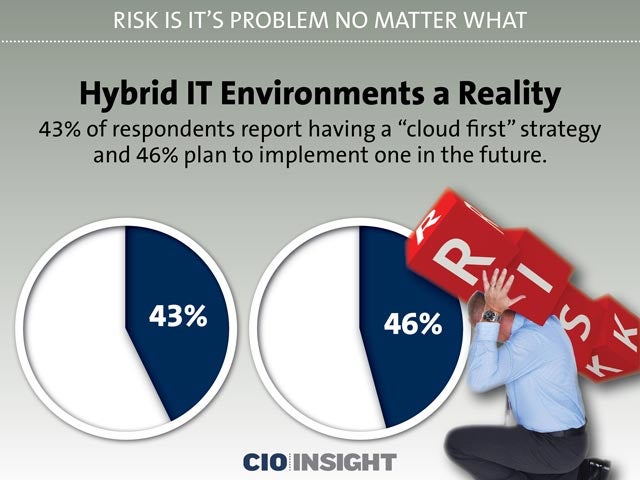 Hybrid IT Environments a Reality
Hybrid IT Environments a Reality
43% of respondents report having a “cloud first” strategy and 46% plan to implement one in the future.
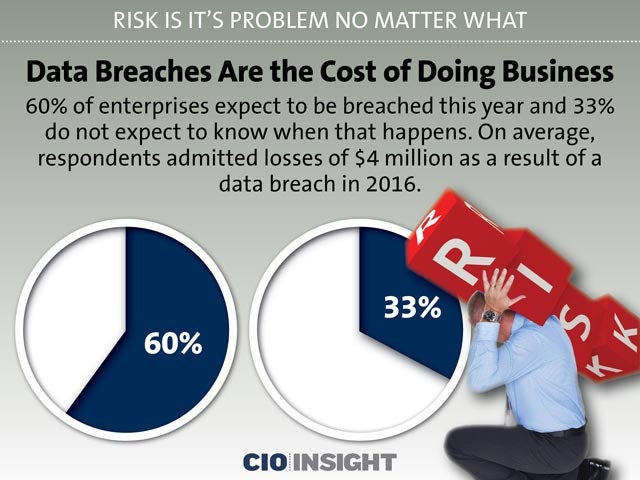 Data Breaches Are the Cost of Doing Business
Data Breaches Are the Cost of Doing Business
60% of enterprises expect to be breached this year and 33% do not expect to know when that happens. On average, respondents admitted losses of $4 million as a result of a data breach in 2016.
 Identity Is Key
Identity Is Key
87% of respondents recognized the importance of having strong identity governance controls across the organization’s entire IT infrastructure.
 Emerging Exposure Points
Emerging Exposure Points
Unstructured data (emails, files, documents, PDFs, etc.) resides outside applications and the structured corporate system, making it harder to manage. It is not always clear who has access to that data.
 Hazards of Safeguarding Unstructured Data
Hazards of Safeguarding Unstructured Data
60% of respondents are concerned about managing and safeguarding sensitive data in such files and 70% believe they are not equipped to fully protect it.