
Most Databases in the Cloud Are Not Encrypted
 Most Databases in the Cloud Are Not Encrypted
Most Databases in the Cloud Are Not Encrypted
In violation of security best practices, the majority of databases in the public cloud are not encrypted, rendering companies vulnerable to cyber-attacks.
 Unencrypted Sensitive Data
Unencrypted Sensitive Data
82% of databases in the public cloud, such as the Amazon Relational Database Service and Amazon RedShift, are not encrypted.
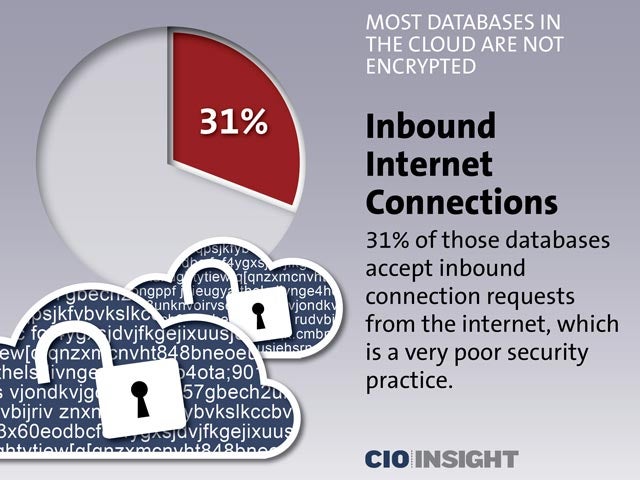 Inbound Internet Connections
Inbound Internet Connections
31% of those databases accept inbound connection requests from the internet, which is a very poor security practice.
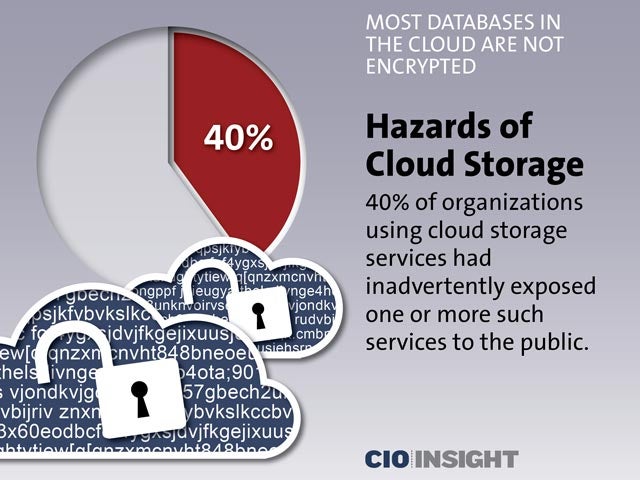 Hazards of Cloud Storage
Hazards of Cloud Storage
40% of organizations using cloud storage services had inadvertently exposed one or more such services to the public.
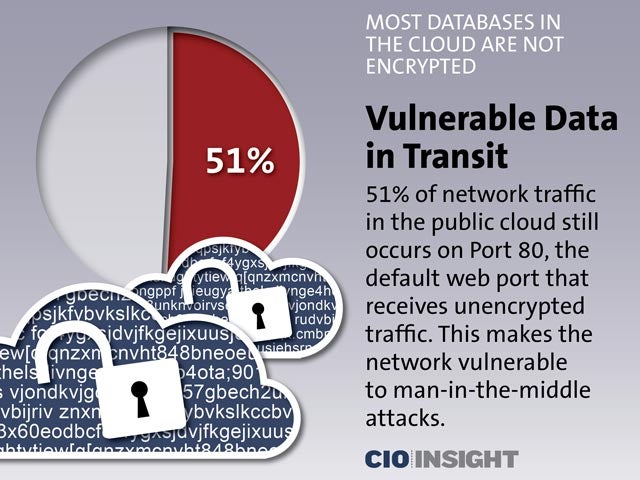 Vulnerable Data in Transit
Vulnerable Data in Transit
51% of network traffic in the public cloud still occurs on Port 80, the default web port that receives unencrypted traffic. This makes the network vulnerable to man-in-the-middle attacks.
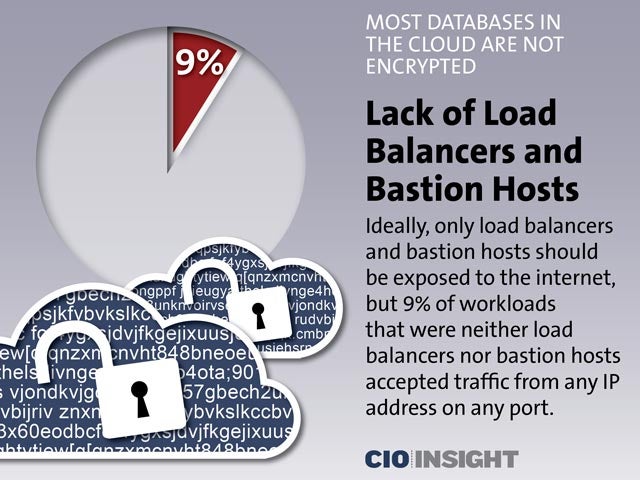 Lack of Load Balancers and Bastion Hosts
Lack of Load Balancers and Bastion Hosts
Ideally, only load balancers and bastion hosts should be exposed to the internet, but 9% of workloads that were neither load balancers nor bastion hosts accepted traffic from any IP address on any port.
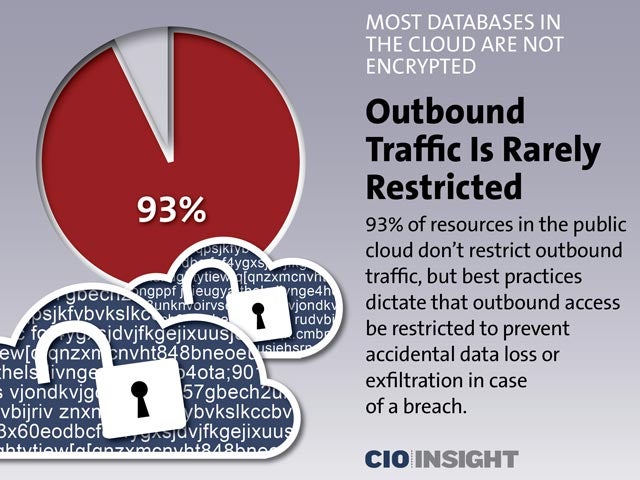 Outbound Traffic Is Rarely Restricted
Outbound Traffic Is Rarely Restricted
93% of resources in the public cloud don’t restrict outbound traffic, but best practices dictate that outbound access be restricted to prevent accidental data loss or exfiltration in case of a breach.
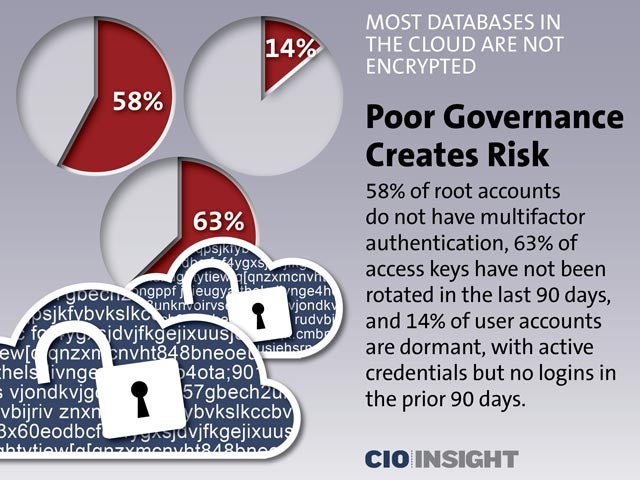 Poor Governance Creates Risk
Poor Governance Creates Risk
58% of root accounts do not have multifactor authentication, 63% of access keys have not been rotated in the last 90 days, and 14% of user accounts are dormant, with active credentials but no logins in the prior 90 days.
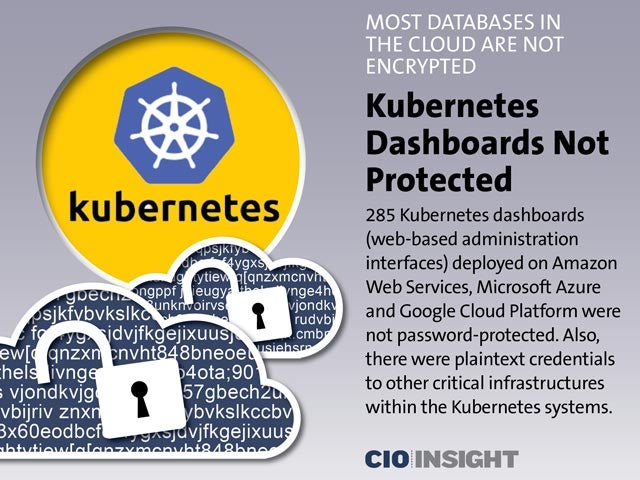 Kubernetes Dashboards Not Protected
Kubernetes Dashboards Not Protected
285 Kubernetes dashboards (web-based administration interfaces) deployed on Amazon Web Services, Microsoft Azure and Google Cloud Platform were not password-protected. Also, there were plaintext credentials to other critical infrastructures within the Kubernetes systems.
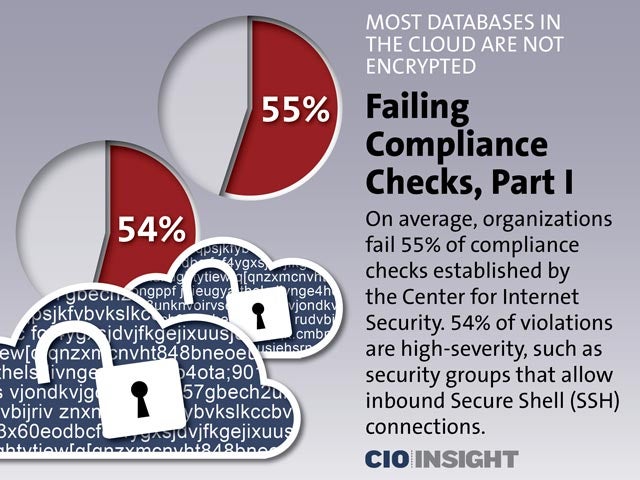 Failing Compliance Checks, Part I
Failing Compliance Checks, Part I
On average, organizations fail 55% of compliance checks established by the Center for Internet Security. 54% of violations are high-severity, such as security groups that allow inbound Secure Shell (SSH) connections.
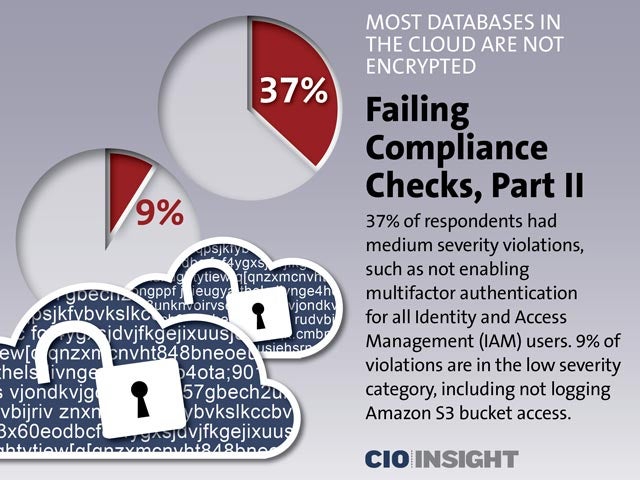 Failing Compliance Checks, Part II
Failing Compliance Checks, Part II
37% of respondents had medium severity violations, such as not enabling multifactor authentication for all Identity and Access Management (IAM) users. 9% of violations are in the low severity category, including not logging Amazon S3 bucket access.