
Safeguard Email From Internal and External Threats
 Safeguard Email From Internal and External Threats
Safeguard Email From Internal and External Threats
Email continues to be a major source of cyber-attacks, and security and risk officers need to be more aware of both outside attackers and internal threats.
 Information Theft Via Email
Information Theft Via Email
33% of the security and risk professionals surveyed have experienced information loss, theft or attack via email within the last two years.
 The Breakout of Attacks
The Breakout of Attacks
Phishing attacks leading to malware infection or data loss: 44%,
Business email compromise or impersonation: 40%,
Insiders emailing sensitive data outside the company: 36%
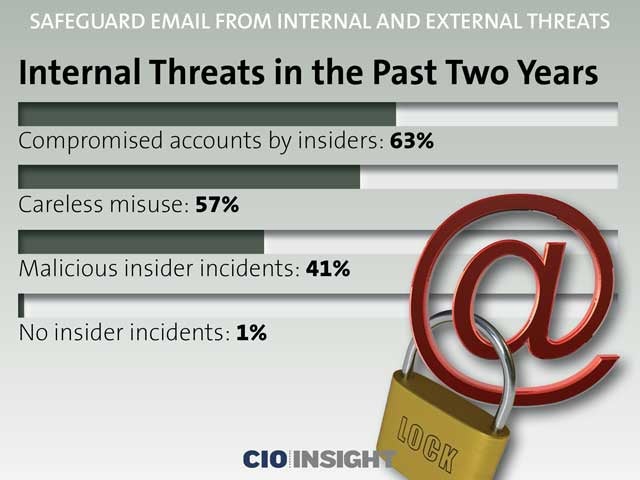 Internal Threats in the Past Two Years
Internal Threats in the Past Two Years
Compromised accounts by insiders: 63%,
Careless misuse: 57%,
Malicious insider incidents: 41%,
No insider incidents: 1%
 The Phishing Threat
The Phishing Threat
Four out of 10 companies surveyed reported a phishing attack in the past two years.
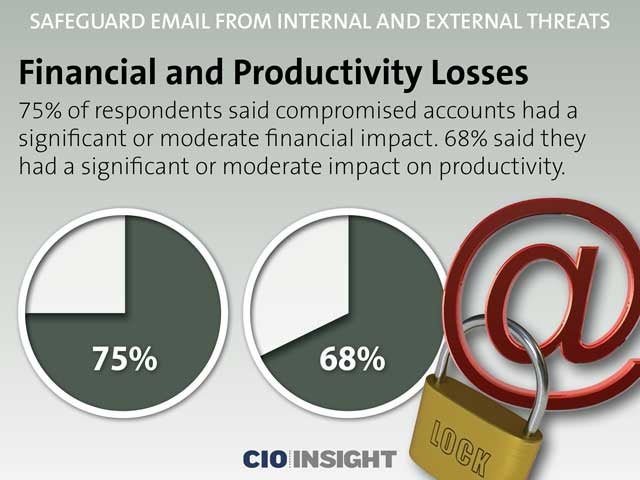 Financial and Productivity Losses
Financial and Productivity Losses
75% of respondents said compromised accounts had a significant or moderate financial impact. 68% said they had a significant or moderate impact on productivity.
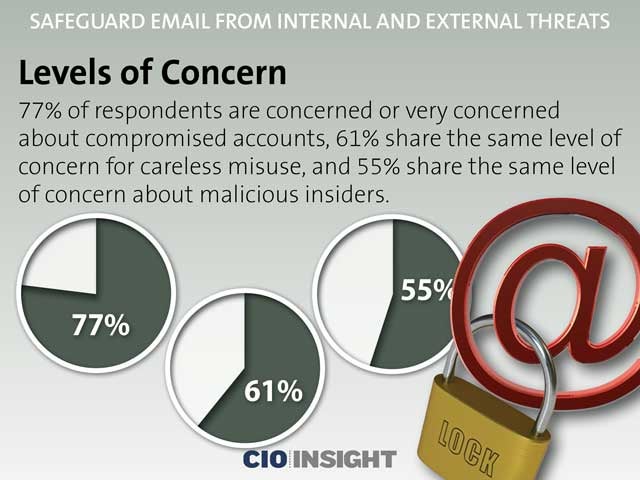 Levels of Concern
Levels of Concern
77% of respondents are concerned or very concerned about compromised accounts, 61% share the same level of concern for careless misuse, and 55% share the same level of concern about malicious insiders.
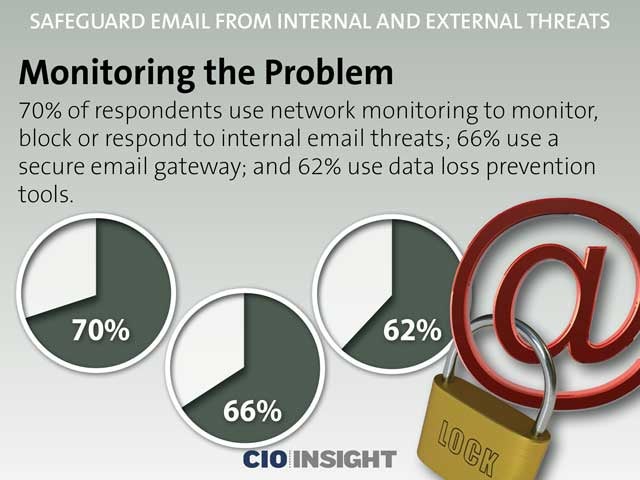 Monitoring the Problem
Monitoring the Problem
70% of respondents use network monitoring to monitor, block or respond to internal email threats; 66% use a secure email gateway; and 62% use data loss prevention tools.
 Old Technologies Used for New Threats, Part 1
Old Technologies Used for New Threats, Part 1
Anti-spam: 62%,
Anti-virus: 57%,
Anti-phishing: 52%,
Privacy controls: 48%,
Data loss prevention inspection: 45%
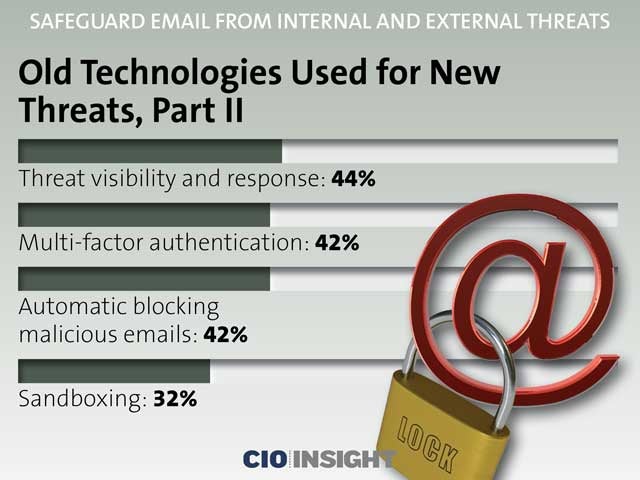 Old Technologies Used for New Threats, Part 11
Old Technologies Used for New Threats, Part 11
Threat visibility and response: 44%,
Multi-factor authentication: 42%,
Automatic blocking malicious emails: 42%,
Sandboxing: 32%
 New Tactics Overlooked
New Tactics Overlooked
Sandboxing, multifactor authentication and automatic blocking of malicious emails are critical to defend against sophisticated attacks, yet fewer respondents are using these security tools.