
New Cyber-Security Model Spurs Innovation
 New Cyber-Security Model Spurs Innovation
New Cyber-Security Model Spurs Innovation
A new model for cyber-security acts on analytic inputs and adapts to evolving threats. It includes analytics, real-time monitoring and advanced authentication.
 Ways to Address Threats and Create Value
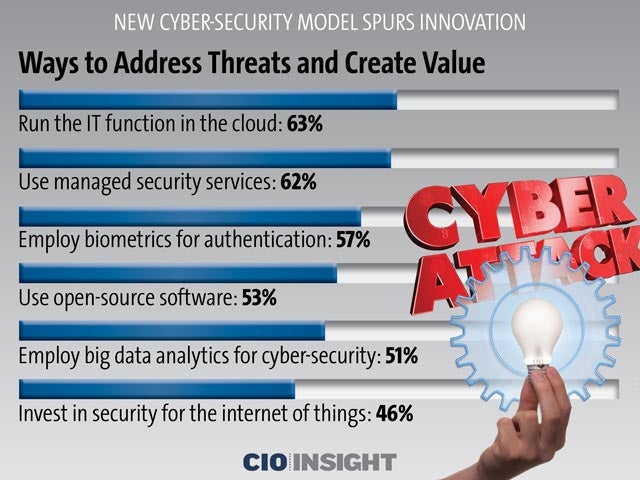
Ways to Address Threats and Create Value
Run the IT function in the cloud: 63% Use managed security services: 62%, Employ biometrics for authentication: 57%, Use open-source software: 53%, Employ big data analytics for cyber-security: 51%, Invest in security for the internet of things: 46%,
 Cyber-Security Spending Priorities for the Next 12 Months
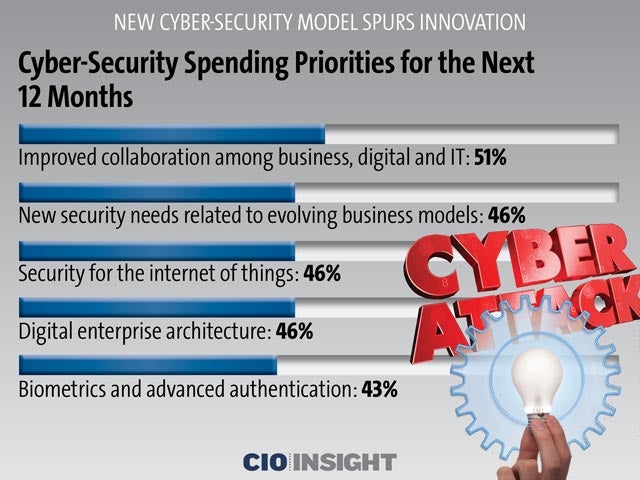
Cyber-Security Spending Priorities for the Next 12 Months
Improved collaboration among business, digital and IT: 51%, New security needs related to evolving business models: 46%, Security for the internet of things: 46%, Digital enterprise architecture: 46%, Biometrics and advanced authentication: 43%
 Trusting the Cloud
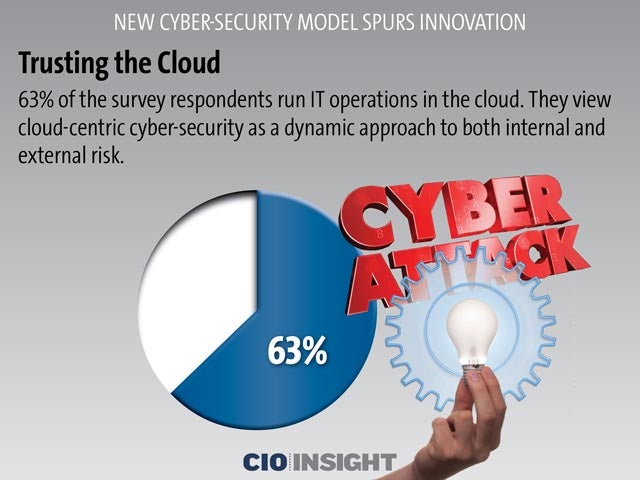
Trusting the Cloud
63% of the survey respondents run IT operations in the cloud. They view cloud-centric cyber-security as a dynamic approach to both internal and external risk.
 Business Functions Run in the Cloud
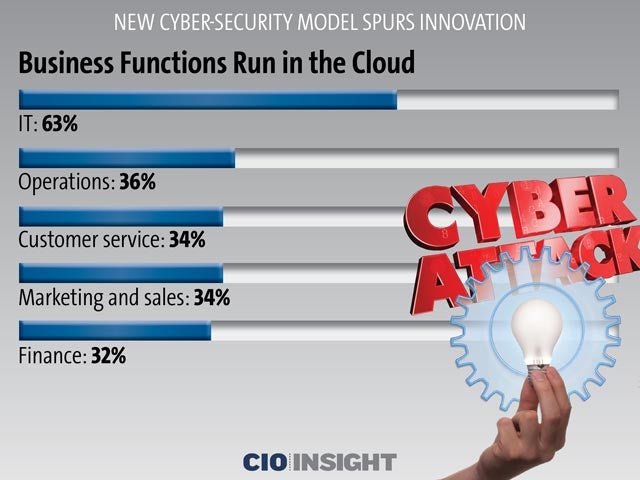
Business Functions Run in the Cloud
IT: 63%, Operations: 36%, Customer service: 34%, Marketing and sales: 34%, Finance: 32%
 Dealing With Security and Privacy
Dealing With Security and Privacy
62% of the respondents use managed security services (MSS) for cyber-security and privacy because of a dearth of skilled cyber-security specialists.
 Using Managed Security Services
Using Managed Security Services
Authentication: 64%, Data loss prevention: 61%, Identity and access management: 61%, Real-time monitoring and analytics: 55%, Threat intelligence: 48%
 Modeling Threats, Identifying Incidents
Modeling Threats, Identifying Incidents
51% of respondents said they use big data analytics to model cyber-security threats and identify incidents. This helps them deal with the scarcity of cyber-security pros and budget constraints.
 From Passwords to Authentication
From Passwords to Authentication
Authentication technologies like biometrics are adding a next layer of security to passwords. 57% of respondents use biometrics, and 46% of them said it’s made online transactions more secure.
 Enhancing Cyber-Security
Enhancing Cyber-Security
53% of the respondents use open-source software, and 49% of them said it has improved their cyber-security program.
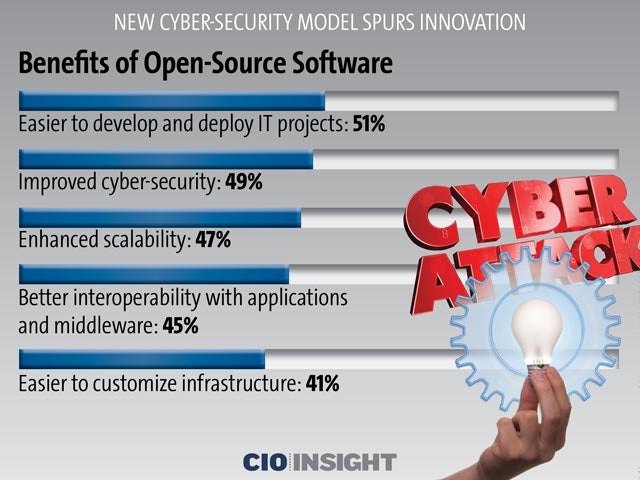 Benefits of Open-Source Software
Benefits of Open-Source Software
Easier to develop and deploy IT projects: 51%, Improved cyber-security: 49%, Enhanced scalability: 47%, Better interoperability with applications and middleware: 45%, Easier to customize infrastructure: 41%