
Unstructured Data, Unending Security Concerns
 Unstructured Data, Unending Security Concerns
Unstructured Data, Unending Security Concerns
IT pros are concerned that unstructured data moving through its lifecycle will yield more data privacy breaches and complicate advanced content management systems.
 Widespread Concern About File Data Leakage Risks
Widespread Concern About File Data Leakage Risks
All organizations surveyed are concerned about file data leakage risks, with 75% expressing high- to very-high concern.
 Pervasive Low Confidence in Security Controls
Pervasive Low Confidence in Security Controls
84% of respondents have moderate to no confidence in their security controls and auditing capacity to secure confidential files.
 Majority Experience File Data Leakage
Majority Experience File Data Leakage
80% of respondents have experienced file data leakage in their organizations. Half have had frequent incidents.
 Top Causes of Data Leakage
Top Causes of Data Leakage
The most likely causes of data leakage are: inappropriate file sharing with others inside the organization, with those outside, and due to malware and hackers.
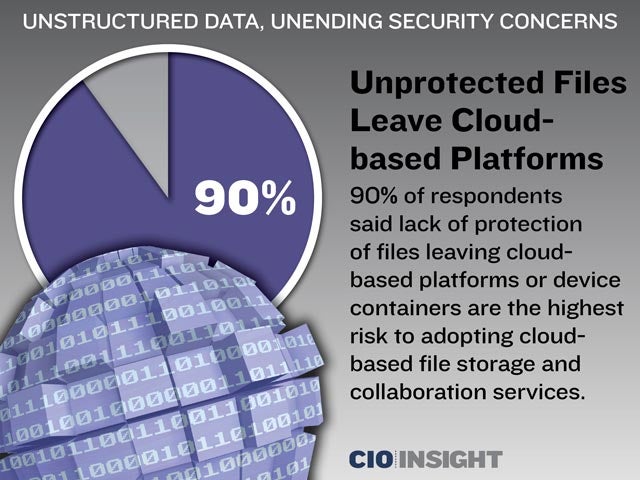 Unprotected Files Leave Cloud-based Platforms
Unprotected Files Leave Cloud-based Platforms
90% of respondents said lack of protection of files leaving cloud-based platforms or device containers are the highest risk to adopting cloud-based file storage and collaboration services.
 Increased Training and Security Technology Purchases Planned
Increased Training and Security Technology Purchases Planned
Organizations expect to increase user awareness training and to purchase additional security technology to combat data leakage.
 Top Control Investments
Top Control Investments
Email Gateway/Proxy and Data Loss Prevention technologies are the top mature controls, while file encryption and usage control software are cited as the top upcoming control investment.
 Users Can Help If Empowered
Users Can Help If Empowered
70% of respondents believe users would use stronger security controls on files they share if they were empowered to do so.
 Best Way to Secure File Data
Best Way to Secure File Data
Respondents said the most significant issue for them is how to secure data leaving the cloud sharing repository and how to secure it once it leaves the container.
 Top Five Encryption Control Concerns
Top Five Encryption Control Concerns
Asked to identify their top concerns using file encryption, respondents indicated the following: Key Management: 86%, Encryption Strength: 85%, Impact to Data Recipients: 83%, Impact to Operational Workflows: 81%, Interoperability with Applications and Infrastructure: 81%