
What Happens to Stolen, Sensitive Data?
 What Happens to Stolen, Sensitive Data?
What Happens to Stolen, Sensitive Data?
An experiment that leaked a fake bank employee’s data to the dark Web shows what happened to the data during its first month out in the open.
 Immediate Spike in Activity
Immediate Spike in Activity
When the credentials were leaked, a rush of hackers tested the fake bank employee’s Google Drive credentials in several of the victim’s other accounts. They quickly downloaded files, including those with real credit card information.
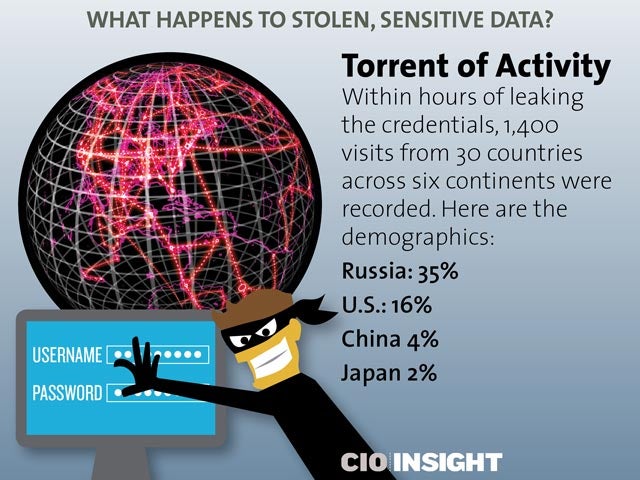 Torrent of Activity
Torrent of Activity
Within hours of leaking the credentials, 1,400 visits from 30 countries across six continents were recorded. Here are the demographics: Russia: 35%, U.S.: 16%, China 4%, Japan 2%
 Logins to Fake Bank
Logins to Fake Bank
One-tenth of the hackers who viewed the credentials tried to log into the bank Web portal.
 Hacked Once, Hacked Everywhere
Hacked Once, Hacked Everywhere
The fictitious bank employee used the same password for personal banking accounts and social media sites. Once hackers used leaked credentials to access his Google Drive, most used those same credentials elsewhere.
 Other Accounts Accessed
Other Accounts Accessed
36% of hackers successfully accessed the victim’s personal banking account using the leaked password. There were recurring logins, some within hours of one another and others weeks after the initial login.
 The Numbers
The Numbers
94% of hackers uncovered and attempted to log into other accounts. Five tried bank logins within the first 24 hours. Three attempted Google Drive logins in the first 24 hours. Within 48 hours, the first file was downloaded.
 The Power of TOR
The Power of TOR
68% of hackers accessed both the Google Drive and the bank portal from TOR-anonymized IP addresses.
 Hackers More Security Conscious Than Ever
Hackers More Security Conscious Than Ever
The high rate of TOR usage indicates that hackers are becoming more security conscious and know to mask their IP’s whenever possible to avoid getting caught.
 Other Occurrences
Other Occurrences
Hackers changed the victim’s password. They made several attempts to crawl the Google Drive, using third-party apps. Some downloaded files did not appear sensitive, including lunch menus.