
Hackers Increasingly Spoof Authentic Identities
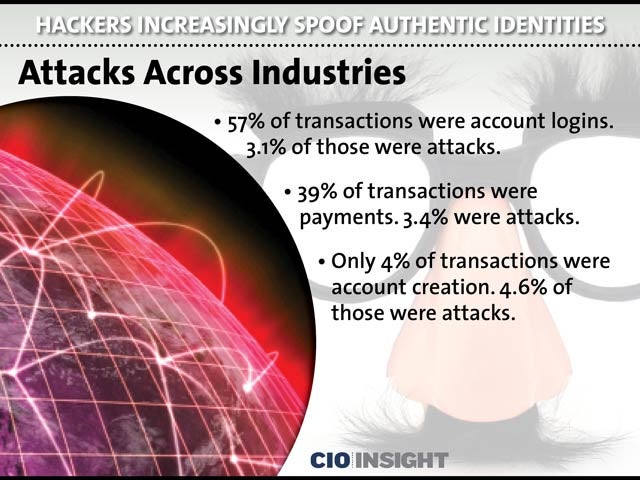 Attacks Across Industries
Attacks Across Industries
57% of transactions were account logins. 3.1% of those were attacks. 39% of transactions were payments. 3.4% were attacks. Only 4% of transactions were account creation. 4.6% of those were attacks.
 Fraud to Move From POS to Online
Fraud to Move From POS to Online
As the U.S. moves toward end-to-end point-of-sale (POS) encryption and “chip and signature” (EMV), POS fraud will transition to online fraud, as it has done in Europe.
 Transactions Analyzed by Industry
Transactions Analyzed by Industry
44% of financial services transactions were analyzed. Attacks: 1%, 31% from e-commerce. Attacks: 4%, 25% from media customers. Attacks: 9%
 Problems With Stored Credit Card Info
Problems With Stored Credit Card Info
Fraud attacks from card-not-present chargebacks have expanded to account takeovers through email addresses and shared passwords for authentication. Although stored credit card information is convenient, it’s an easy target for criminals.
 Online Authentications Plague Banks
Online Authentications Plague Banks
Financial institutions have shifted from detecting irregular account access to stopping valid customers from being “caught in the fraud net.” Without automated real-time analysis, banks cannot discern legitimate logins from fraudulent ones, so they are using people to review alerts.
 Media: Most Attacks Per Transaction
Media: Most Attacks Per Transaction
Because only an email address and password are required by media sites, they suffer the highest rate of attacks per transaction. Most are fraudulent account logins motivated by the potential to reach large audiences for advertising, distributing malware and confidence scams.
 Spoofing Is Top Attack Method
Spoofing Is Top Attack Method
Device spoofing: 6.2%, Identity spoofing: 4.7%, Geographic spoofing: 2.7%, IP spoofing: 2.3%, Man-in-the-Browser or BOT: 2.1%
 Spoofing by Transaction Type
Spoofing by Transaction Type
Spoofing is the most frequent type of attack across transactions. Device and identity spoofing were most frequent, with account creation enduring 5.2% and 9.4%, respectively. account logins had 6.4% and 4.7%, and payments had 4.8% and 5.1%.
 Mobile vs. Desktop
Mobile vs. Desktop
Mobile account creation suffers from a disproportionately large share of transactions and attacks. 40% of accounts created were done on mobile, compared with 60% on desktop. 24% in account logins were done on mobile, versus 76% on desktop. 23% of payments were done on mobile, versus 77% on desktop.
 Attacks by Transaction Type
Attacks by Transaction Type
The largest percentage of attacks are experienced on desktops, regardless of the type of transaction. Account creation: mobile: 3.8%, desktop: 5.2%, Account logins: mobile: 1.3%, desktop: 3.6%, Payments: mobile: 2.0%, desktop: 3.8%