
When Security Breaches Come From Within
 Insider Threats Rule
Insider Threats Rule
93% of U.S. respondents say they feel vulnerable to insider attacks. Only 7% feel safe. 59% believe privileged users pose the most threats to their organizations.
 Security Priorities
Security Priorities
Preventing a data breach is the highest or second-highest priority for IT security spending, according to 54% of respondents.
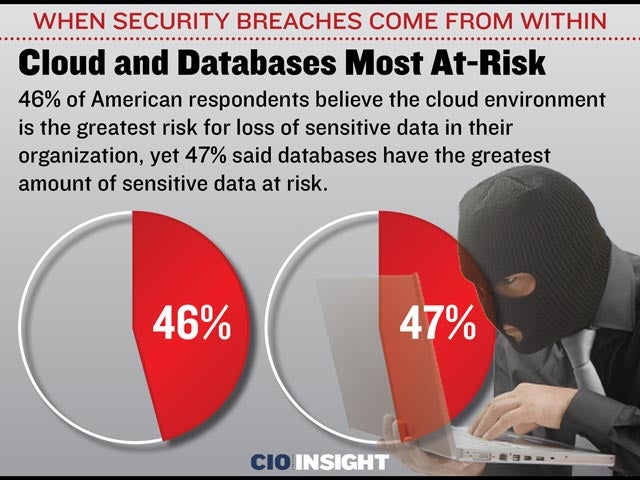 Cloud and Databases Most At-Risk
Cloud and Databases Most At-Risk
46% of American respondents believe the cloud environment is the greatest risk for loss of sensitive data in their organization, yet 47% said databases have the greatest amount of sensitive data at risk.
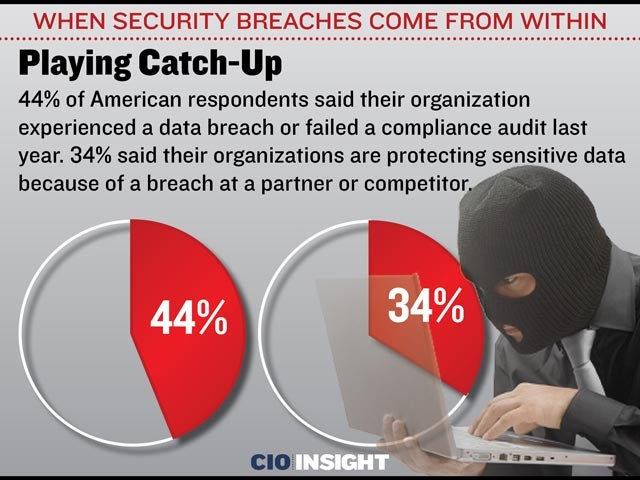 Playing Catch-Up
Playing Catch-Up
44% of American respondents said their organization experienced a data breach or failed a compliance audit last year. 34% said their organizations are protecting sensitive data because of a breach at a partner or competitor.
 Worldwide Perception of Insider Threats
Worldwide Perception of Insider Threats
55% of global respondents believe privileged users are the greatest threat. Contractors and service providers followed at 46%, business partners at 43%.
 Top Three Locations for Most At-Risk Data
Top Three Locations for Most At-Risk Data
The top three places by volume where data is at risk: Databases (47%), File Servers (39%), Cloud (37%)
 Disagreement Over Where Most At-Risk Data Resides
Disagreement Over Where Most At-Risk Data Resides
“Corporate servers and databases pose the highest risk, yet spending remains stubbornly focused on endpoint and mobile,” according to the report. “Only 20% of sensitive company data is held on mobile devices.”
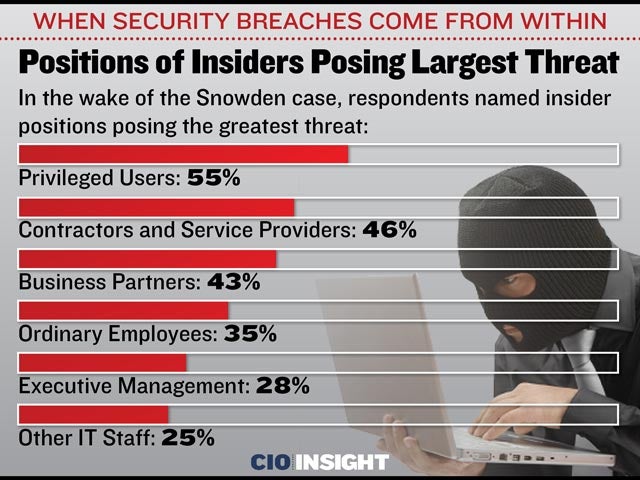 Positions of Insiders Posing Largest Threat
Positions of Insiders Posing Largest Threat
In the wake of the Snowden case, respondents named insider positions posing the greatest threat: Privileged Users: 55%, Contractors and Service Providers: 46%, Business Partners: 43%, Ordinary Employees: 35%, Executive Management: 28%, Other IT Staff: 25%
 Confusion Over What to Protect
Confusion Over What to Protect
Although security spending increased 10% in 2014 and double-digit growth is expected this year, the report said spending is unfocused.
 Dangerous Insiders Have Privileged Access
Dangerous Insiders Have Privileged Access
Only one-half of all businesses have deployed privileged access-identity management technology (PAM or PIM) although there is progress because privileged user access is at the top of senior management’s agenda.
 Recommendations
Recommendations
Address BYOD and mobile data protection concerns through improved data monitoring and increasing data protection through encryption.
 Implement Risk-Based Strategies
Implement Risk-Based Strategies
Rather than spreading funds across a wide range of security protection solutions, the report recommends risk-based strategies for the protection of sensitive data, monitoring and reporting on usage, and controlling user access, including encryption-based data protection and protecting data in transit between corporate systems.