
Why Cyber-Criminals Are Always One Step Ahead
 Why Cyber-Criminals Are Always One Step Ahead
Why Cyber-Criminals Are Always One Step Ahead
Leave-no-trace malware is one way cyber-criminals are able to avoid exposure and remain undetected on company networks for months at a time.
 The Transient Nature of Criminal Infrastructure
The Transient Nature of Criminal Infrastructure
How Pony Loader works: Pony Loader infects a device. Dropper installs and runs. Malware calls the command-and-control server and downloader site. It receives encrypted binaries. Other malware, such as Dyre, Vawtrack and Nyumaim download and infect host device.
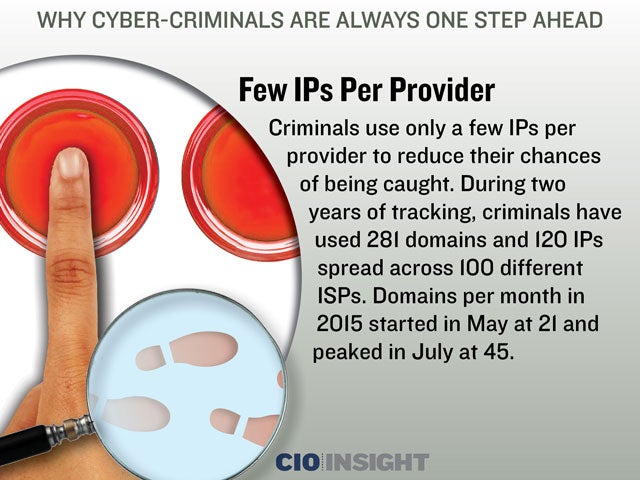 Few IPs Per Provider
Few IPs Per Provider
Criminals use only a few IPs per provider to reduce their chances of being caught. During two years of tracking, criminals have used 281 domains and 120 IPs spread across 100 different ISPs. Domains per month in 2015 started in May at 21 and peaked in July at 45.
 Establishing Infrastructure and Process
Establishing Infrastructure and Process
The number of IPs decreased in July and August, but the number of domains increased significantly cannot compare to the previous months. There were 45 domains in July and 39 in August.
 Domains Per IP Ratio
Domains Per IP Ratio
Domains were divided over 12 IPs in July and over six IP s in August for a ratio of 6.5 domains per IP in August—twice as many as July.
 Why the Inverse Relationship?
Why the Inverse Relationship?
Time of year may be a factor. Europeans take summer vacations in July and August so there are fewer resources available to maintain the infrastructure. The crew may have been heavily using the few ISPs they had while awaiting the return of their cohorts.
 Momentum Regained
Momentum Regained
In September, Pony Loader regained momentum. Criminals used 45 domains over 16 IPs for a ratio of 2.81 domains per IP.
 High Numbers Retained
High Numbers Retained
October also had high numbers: 45 domains divided over 26 IPs for a ratio of 1.73 domains per IP. The number of ISPs was less than two to one with the number of IPs.
 Slowdown Through the Holidays
Slowdown Through the Holidays
In November, the ratio was 2.29 domains per IP. In December the ratio was 2.7. Again, this can be attributed to vacation time.
 Malware Metamorphoses
Malware Metamorphoses
The criminals behind Pony Loader change their malware. In May it was configured to download the banking trojan Dyre. In Septemberm it downloaded Vawtrak, another banking trojan, which was replaced in December with Nymaim, a form of ransomware. Then it flipped back to Vawtrak.
 Pony Loader Group Well-Organized
Pony Loader Group Well-Organized
The criminal group behind Pony Loader regularly creates several new domains establishing new infrastructure, thereby ensuring that most security products cannot detect their new malware.
 Bulletproof Hosters
Bulletproof Hosters
This group uses bulletproof hosters, or providers in non-cooperative countries, and let’s them remain online long enough to switch to different providers, thereby remaining stealthy.
 Bottom Line
Bottom Line
Prevention tools that rely on blacklists and other known indicators will never find these types of attacks. Security teams should look for active command-and-control communications that originate from inside the network and block outbound attempts.